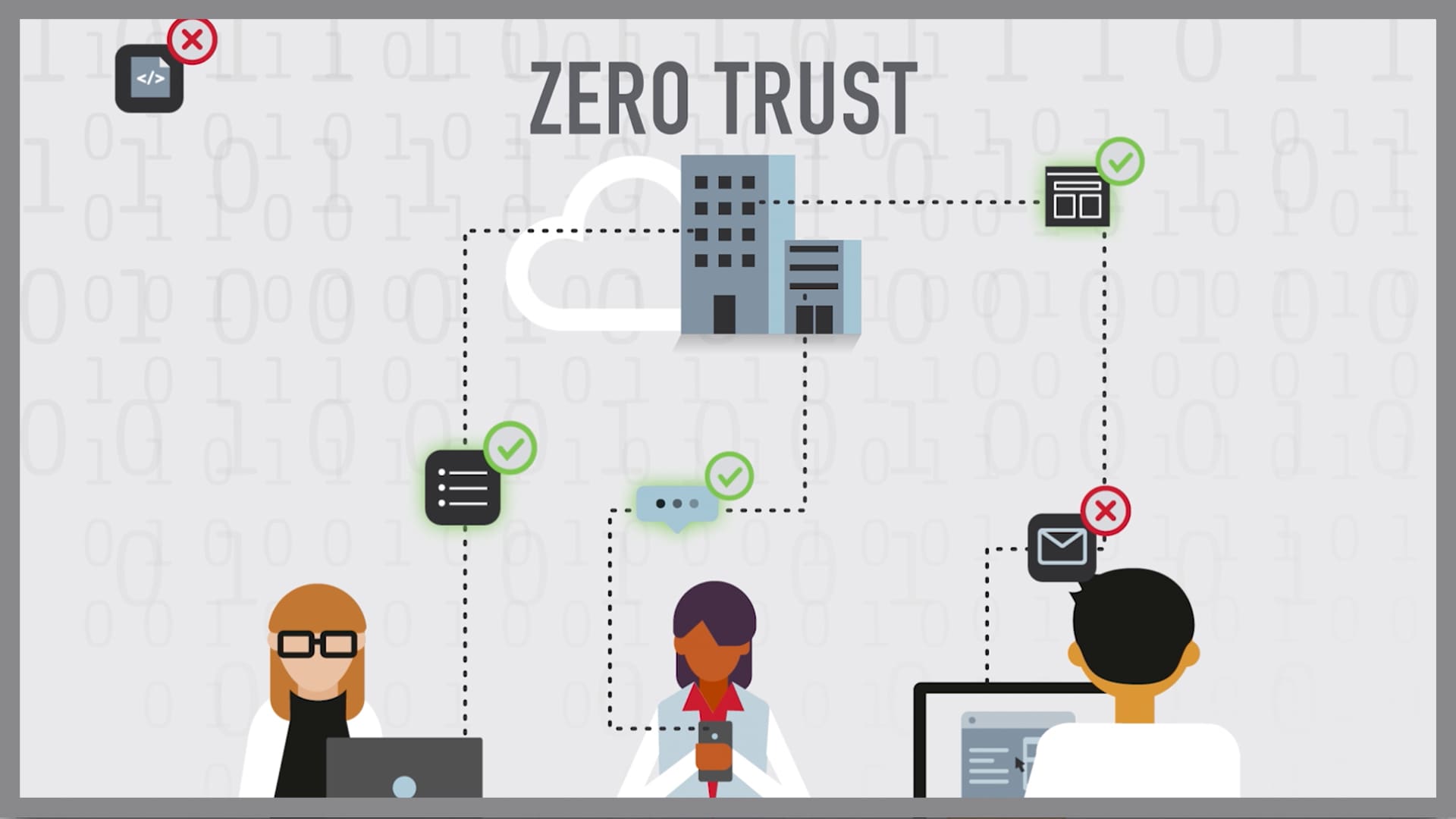
How Does Zero Trust Work Zero trust is a network security philosophy that states no one inside or outside the network should be trusted unless their identification has been thoroughly checked Zero trust operates on the assumption that threats both outside and inside the network are an omnipresent factor
Zero Trust is a security framework requiring all users whether in or outside the organization s network to be authenticated authorized and continuously validated for security configuration and posture before being granted or keeping access to applications and data Understand the Zero Trust security model learn about the principles and apply the Zero Trust architecture using Microsoft 365 and Microsoft Azure services
How Does Zero Trust Work

How Does Zero Trust Work
https://www.microsoft.com/security/blog/wp-content/uploads/2019/11/Zero-Trust-strategy-what-good-looks-like-4.png
Overview Of Zero Trust And How To Get Started
https://goteleport.com/blog/_next/static/media/zero-to-zero-trust-header.9a8602bb.png

Getting Started With ISO 27001 Here s What You Need To Know Data
https://www.manageengine.com/log-management/cyber-security/images/zero-trust-the-journey-towards-secure-network.png
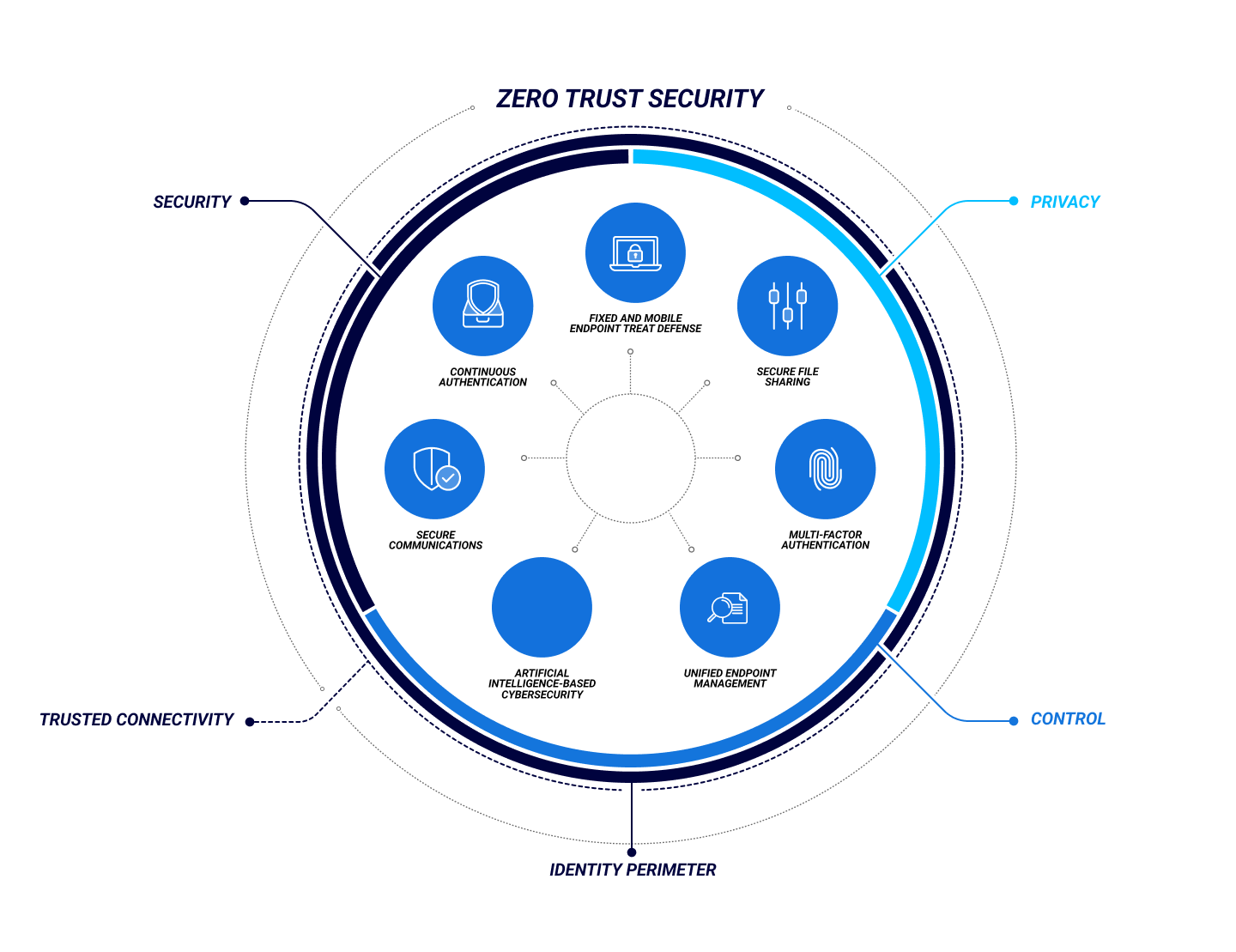
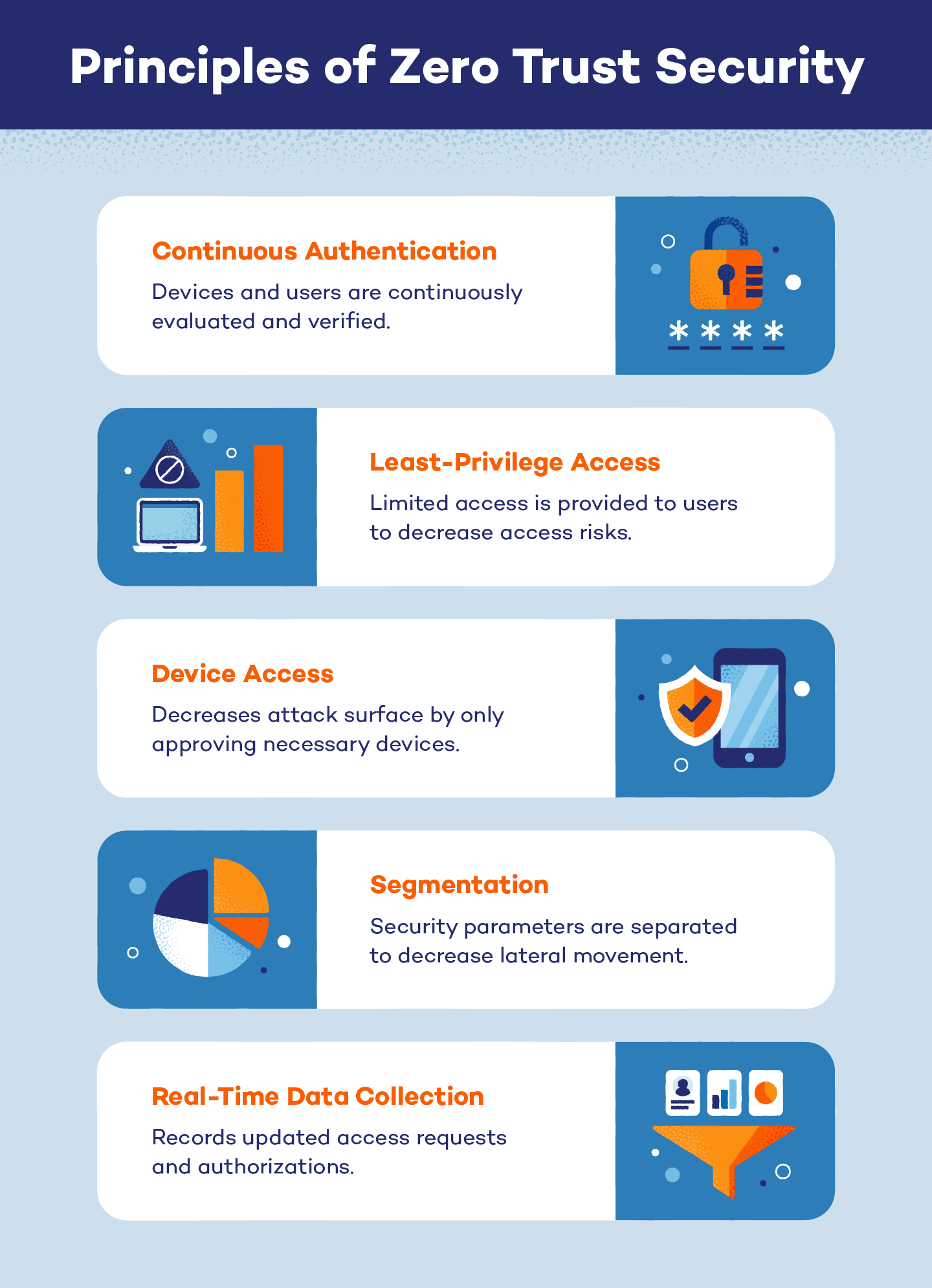
This article outlines what Zero Trust is how Zero Trust works the five core principles of Zero Trust and the stages of implementing Zero Trust security Instead of only guarding an organization s perimeter Zero Trust architecture protects each file email and network by authenticating every identity and device That s why it s also called perimeterless security
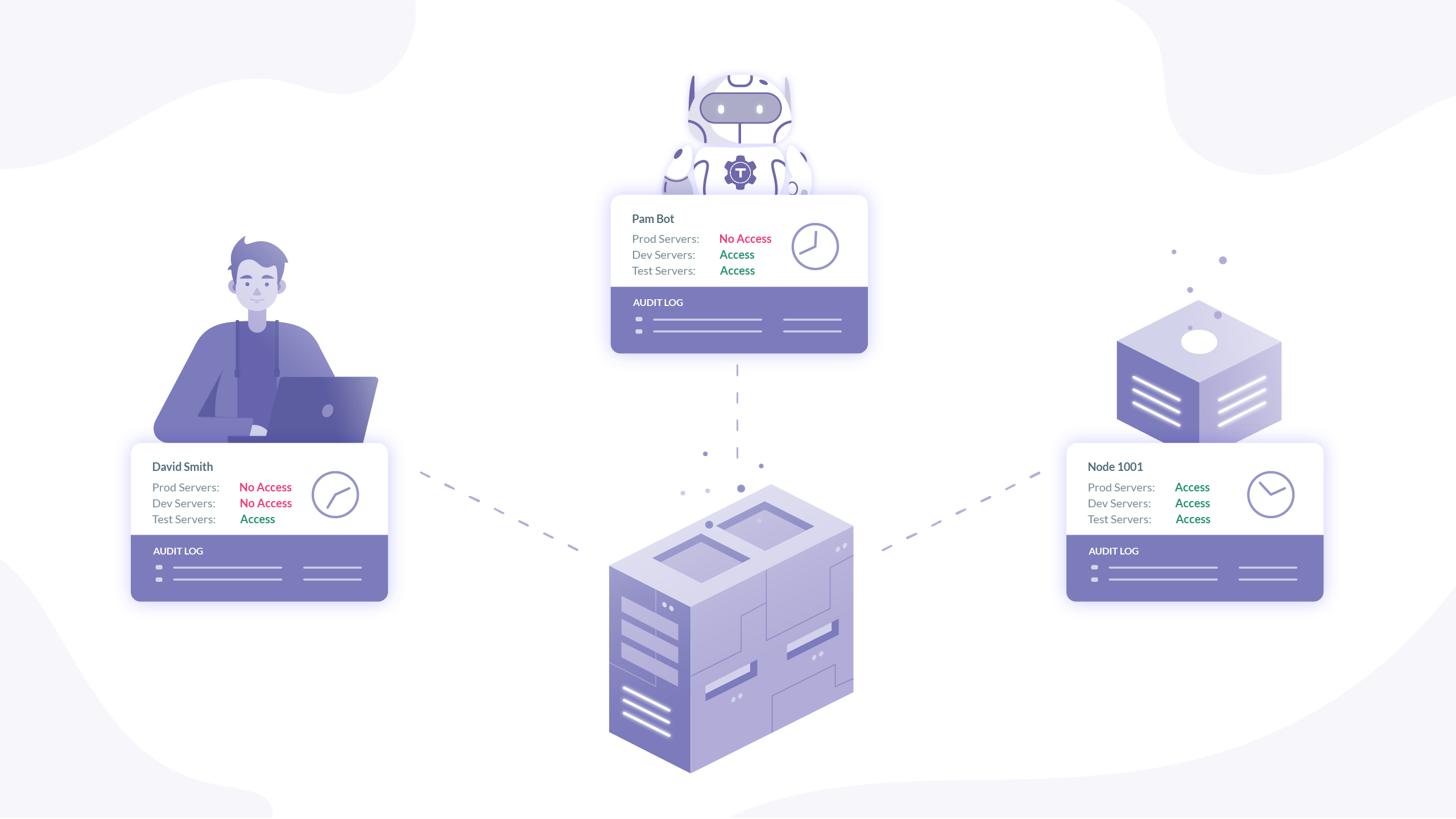
Zero trust is a security strategy that asserts that no entity user app service or device should be trusted by default How Does Zero Trust Work Zero trust works by simply never implicitly trusting a request for data applications or resources and assuming the requester could be a bad actor When you look at security through that lens the result is new levels of granularity in tools and policies
Download How Does Zero Trust Work
More picture related to How Does Zero Trust Work

What Is Zero Trust By Wentz Wu CISSP ISSMP ISSAP ISSEP CCSP CSSLP
https://i0.wp.com/wentzwu.com/wp-content/uploads/2020/10/Zero-Trust-Cybersecurity-Paradigm.jpg?w=4000&ssl=1
What Is Zero Trust Security
https://images.blackberry.com/is/image/blackberry/zero-trust-1440?wid=1440&fmt=png-alpha

What Is Zero Trust Security
https://theinstillery.com/assets/seo/What-is-Zero-Trust-and-how-does-it-work__ResizedImageWzgwMCw0MjBd.png
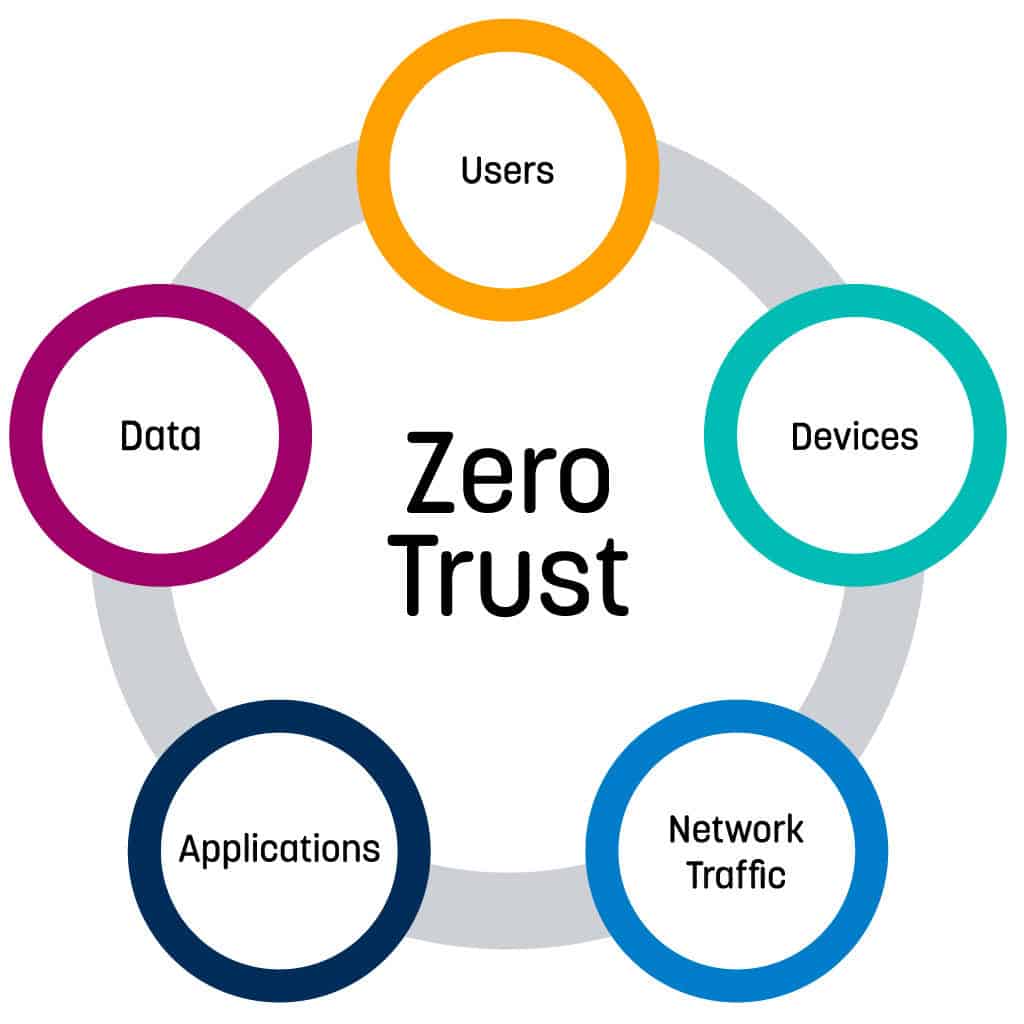
Zero Trust is a strategy for securing critical resources such as databases application servers or devices and machines and the data stored on them by positively and continuously validating the identity of all users and applications that access them Zero Trust is a new security model that assumes breach and verifies each request as though it originated from an uncontrolled network In this article you ll learn about the guiding principles of Zero Trust and find resources to help you implement Zero Trust
[desc-10] [desc-11]
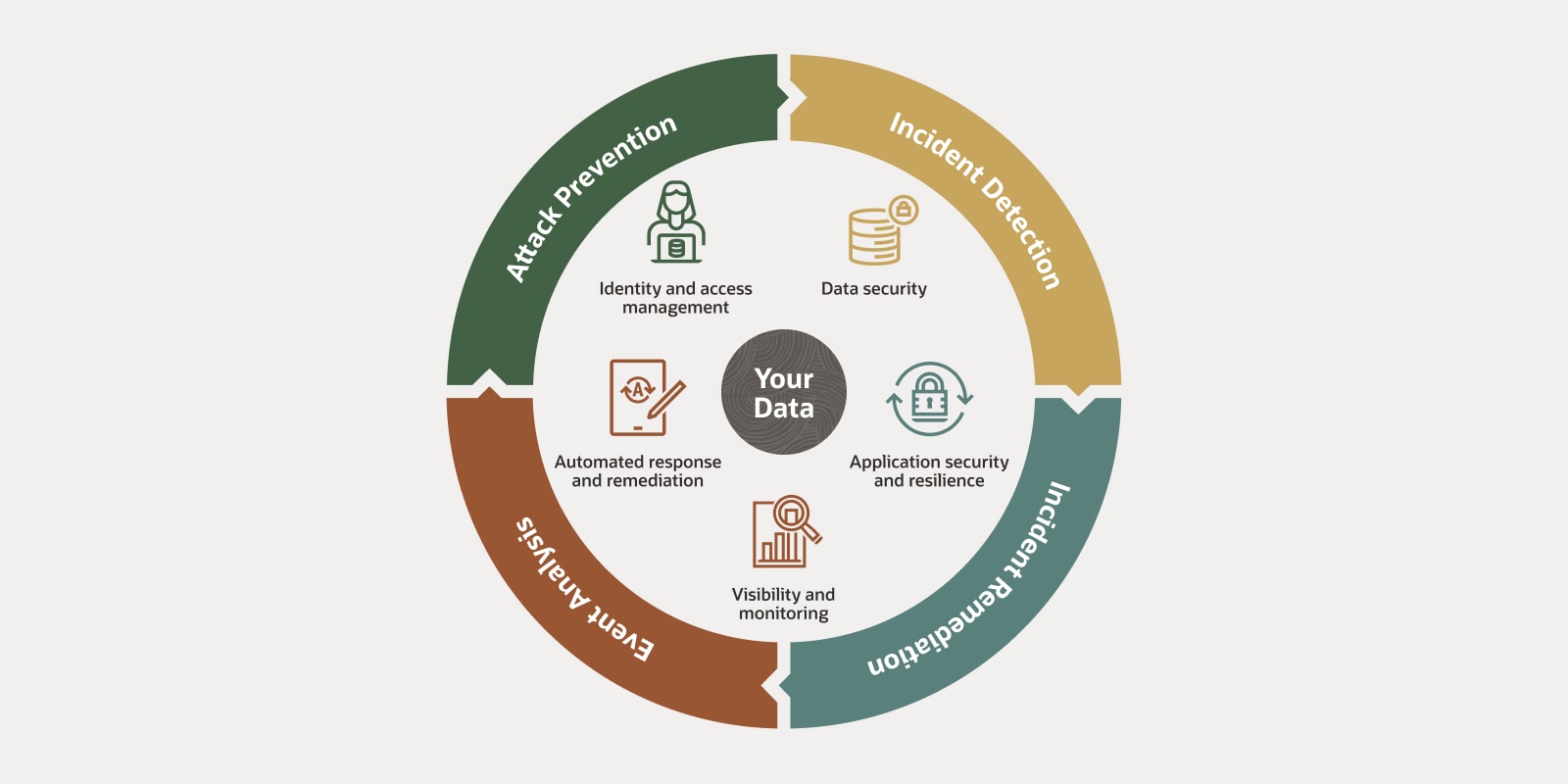
Zero Trust Oracle
https://www.oracle.com/a/ocom/img/cc01-zero-trust-model.jpg
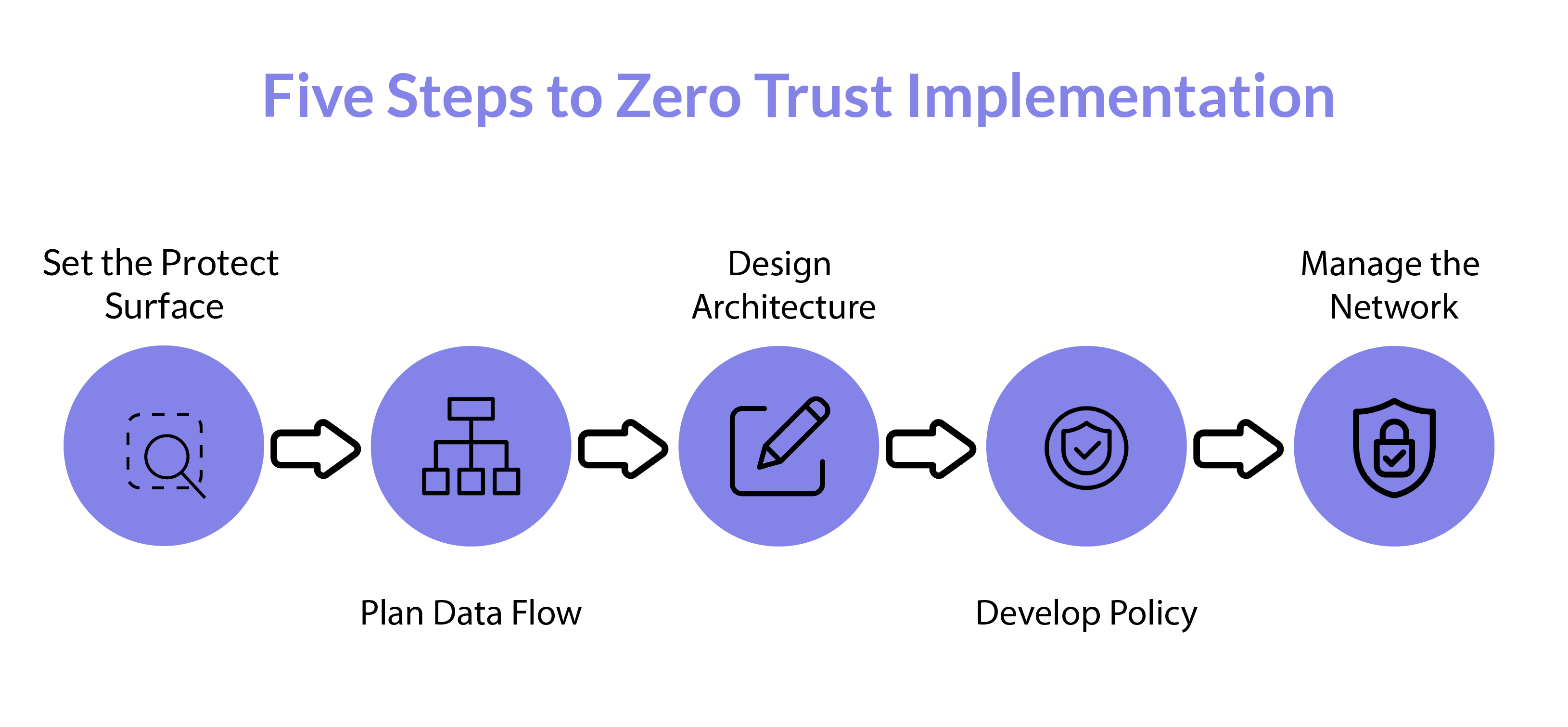
How To Implement Zero Trust Security Geniusee
https://geniusee.com/storage/app/media/blog/blog196_Zero_Trust/ZeroTrusrSteps.png

https://www.fortinet.com/resources/cyberglossary/...
Zero trust is a network security philosophy that states no one inside or outside the network should be trusted unless their identification has been thoroughly checked Zero trust operates on the assumption that threats both outside and inside the network are an omnipresent factor

https://www.crowdstrike.com/.../zero-trust-security
Zero Trust is a security framework requiring all users whether in or outside the organization s network to be authenticated authorized and continuously validated for security configuration and posture before being granted or keeping access to applications and data
What Is Zero Trust Zero Trust Security Model Akamai

Zero Trust Oracle
What Is Zero Trust Security Panda Security

Why You Need 6 Layers Of Zero Trust Control
Microsoft Promoot Mindset Op Zero Trust beveiliging
.jpg?itok=NRhrIEBZ)
What Is Zero Trust And How Does It Work Nasscom The Official
.jpg?itok=NRhrIEBZ)
What Is Zero Trust And How Does It Work Nasscom The Official
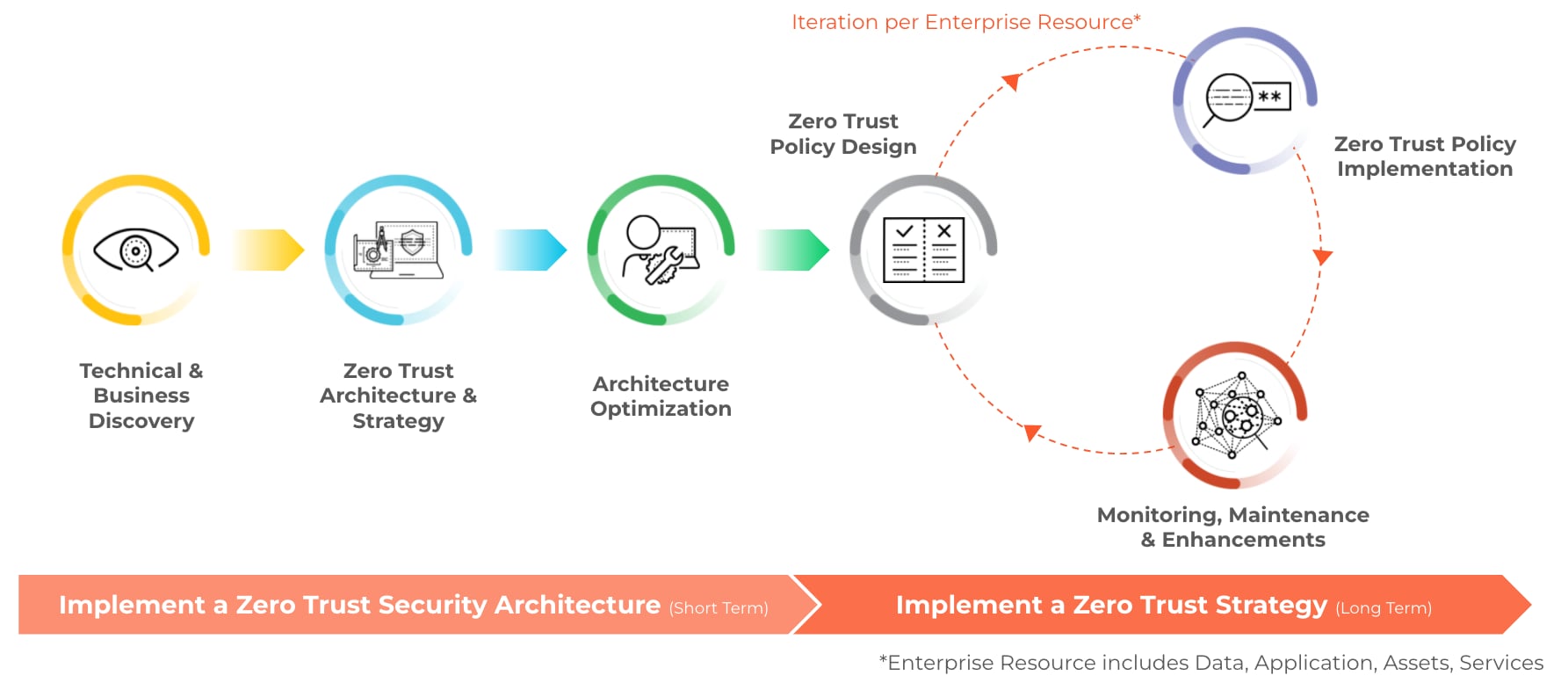
Strategy To Implementation With The Zero Trust Advisory Service Palo

Why Your Organization Needs Zero Trust JumpCloud

Overhauling Zero Trust How To Enforce The Security You Need
How Does Zero Trust Work - [desc-14]