What Is Zero Trust Architecture Zero Trust Architecture ZTA is a security model based on the principle of least privilege Least privilege means that users and devices are only granted the permissions they need to perform their tasks
What are the Core Principles of the Zero Trust Model The Zero Trust model based on NIST 800 207 includes the following core principles Continuous verification Always verify access all the time for all resources Limit the blast radius Minimize impact if an external or insider breach occurs Automate context collection and response The zero trust security model also known as zero trust architecture ZTA zero trust network access ZTNA and perimeterless security describes an approach to the strategy design and implementation of IT systems
What Is Zero Trust Architecture
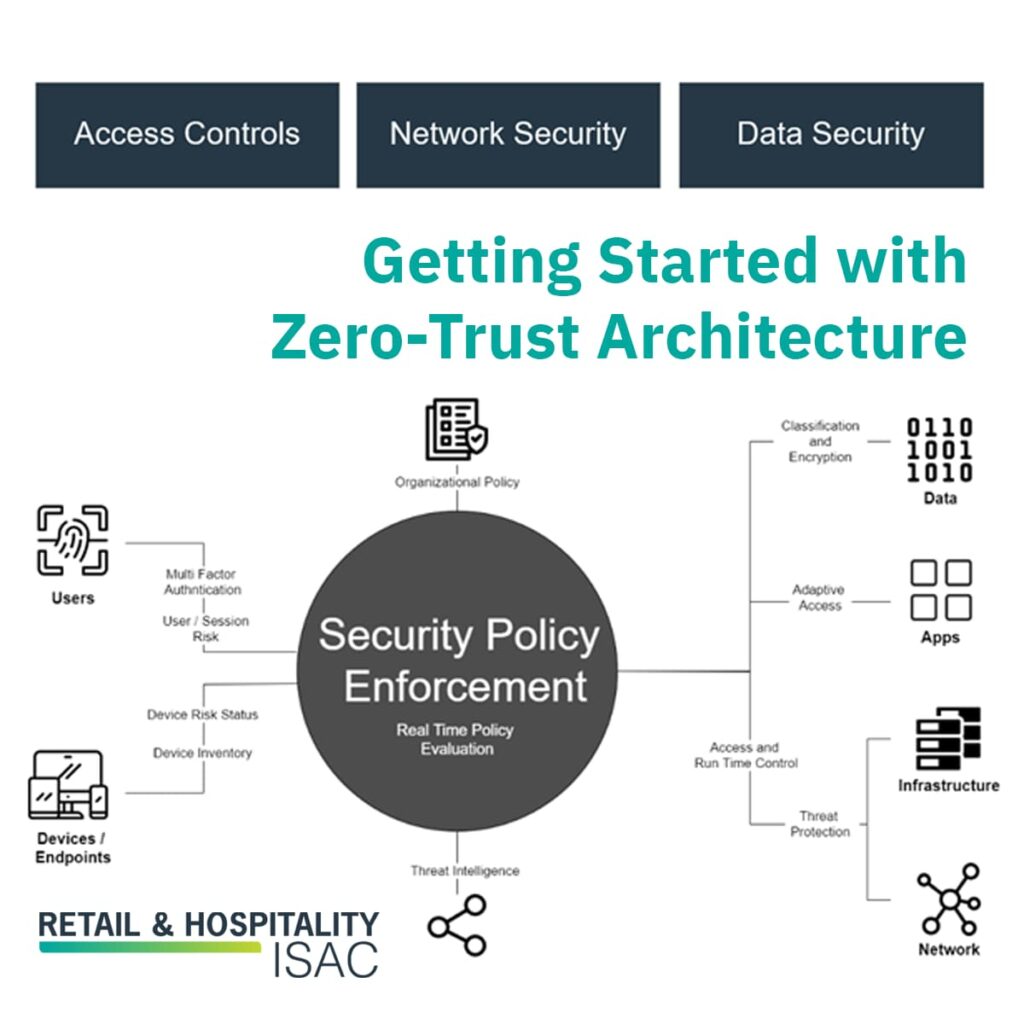
What Is Zero Trust Architecture
https://rhisac.org/wp-content/uploads/Getting-Started-with-Zero-Trust-Architecture-1024x1024.jpg
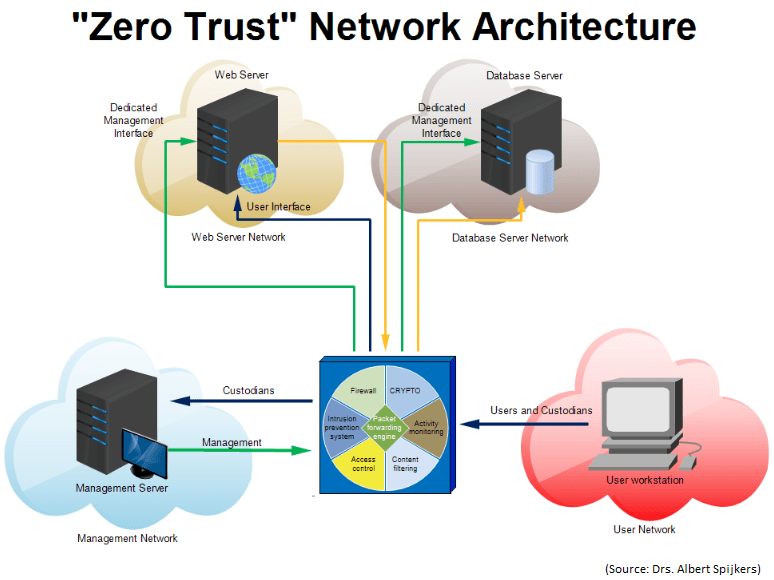
Zero Trust Security Model Alexander s Blog
https://www.zubairalexander.com/blog/wp-content/uploads/2018/02/zero-trust-network-architecture.png

DevSecOps As Part Of Zero Trust Architecture Medium
https://miro.medium.com/v2/resize:fit:1024/1*jF1gs0OlJf9MfjNapQTOVQ.png
Understand the Zero Trust security model learn about the principles and apply the Zero Trust architecture using Microsoft 365 and Microsoft Azure services Zero trust requires planning and executing across a broad range of functional areas including identity and access policies security solutions and workflows automation operations and network infrastructure Many organizations follow specific zero trust frameworks to build zero trust architectures
Zero Trust is a strategic approach to cybersecurity that secures an organization by eliminating implicit trust and continuously validating every stage of a digital interaction Zero Trust is a cloud security model that requires all users no matter affiliation to be authorized and authenticated Learn more here
Download What Is Zero Trust Architecture
More picture related to What Is Zero Trust Architecture

Zero trust model 1 png Microsoft 365 Blog
https://www.microsoft.com/th-th/microsoft-365/blog/wp-content/uploads/sites/59/2019/09/Zero-trust-model-1.png

Is Zero Trust Architecture The Method Of Future Cybersecurity
https://i2.wp.com/oversitesentry.com/wp-content/uploads/2020/05/zerotrustarchitecture-scaled.jpg?resize=1170%2C904&ssl=1
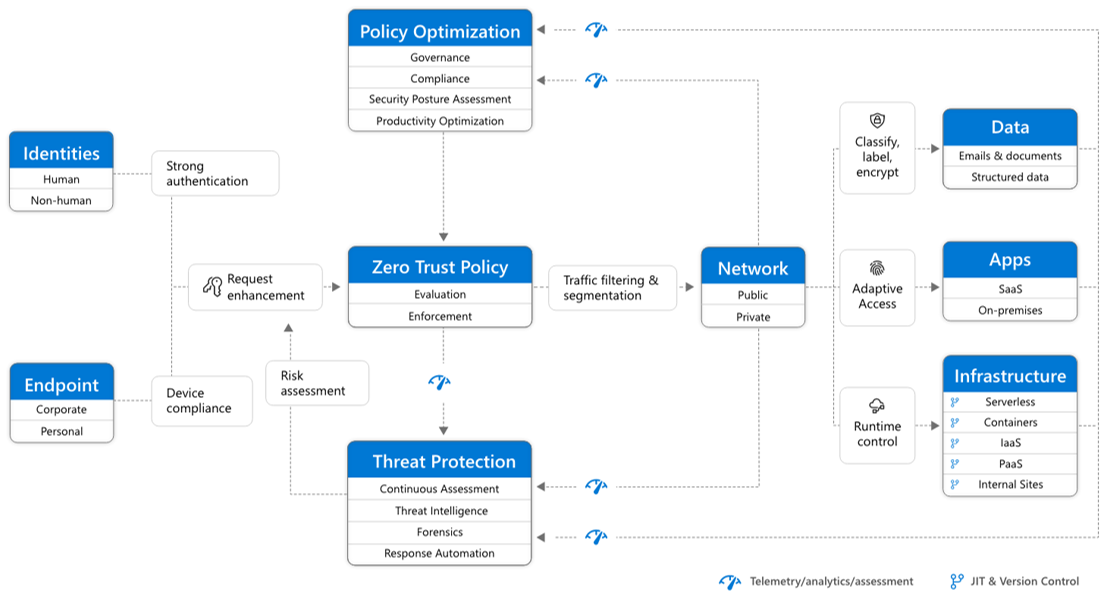
Zero Trust Von Identit ts Und Ger tezugriffskonfigurationen
https://learn.microsoft.com/de-de/microsoft-365/media/zero-trust/zero-trust-architecture.png?view=o365-worldwide
ZTNA is the main technology associated with Zero Trust architecture but Zero Trust is a holistic approach to network security that incorporates several different principles and technologies More simply put traditional IT network security trusts anyone and anything inside the network A Zero Trust Architecture refers to the way network devices and services are structured to enable a Zero Trust security model
[desc-10] [desc-11]
Forrester Zero Trust Model Images And Photos Finder
https://www.infusedinnovations.com/wp-content/uploads/2021/01/zero-trust-model-1-1-1.png
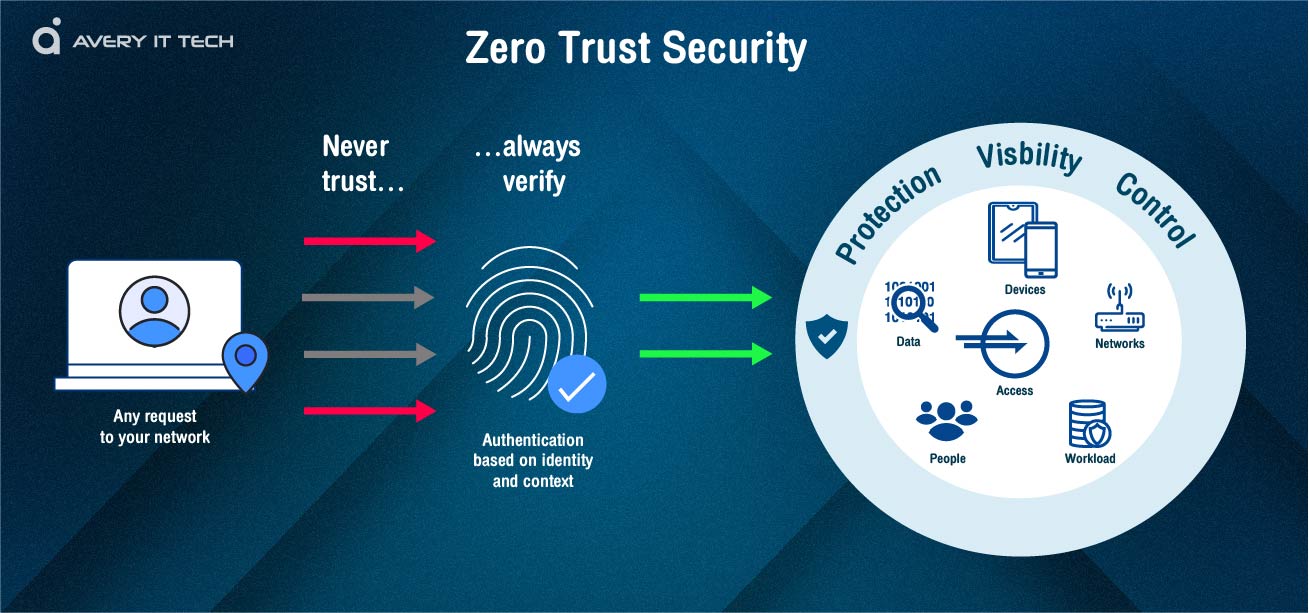
Zero Trust Network Access Concept Averyittech
https://www.averyittech.com/assets/plugins/summernote_gallery/Zero_Trust_Concept_02-05.jpg
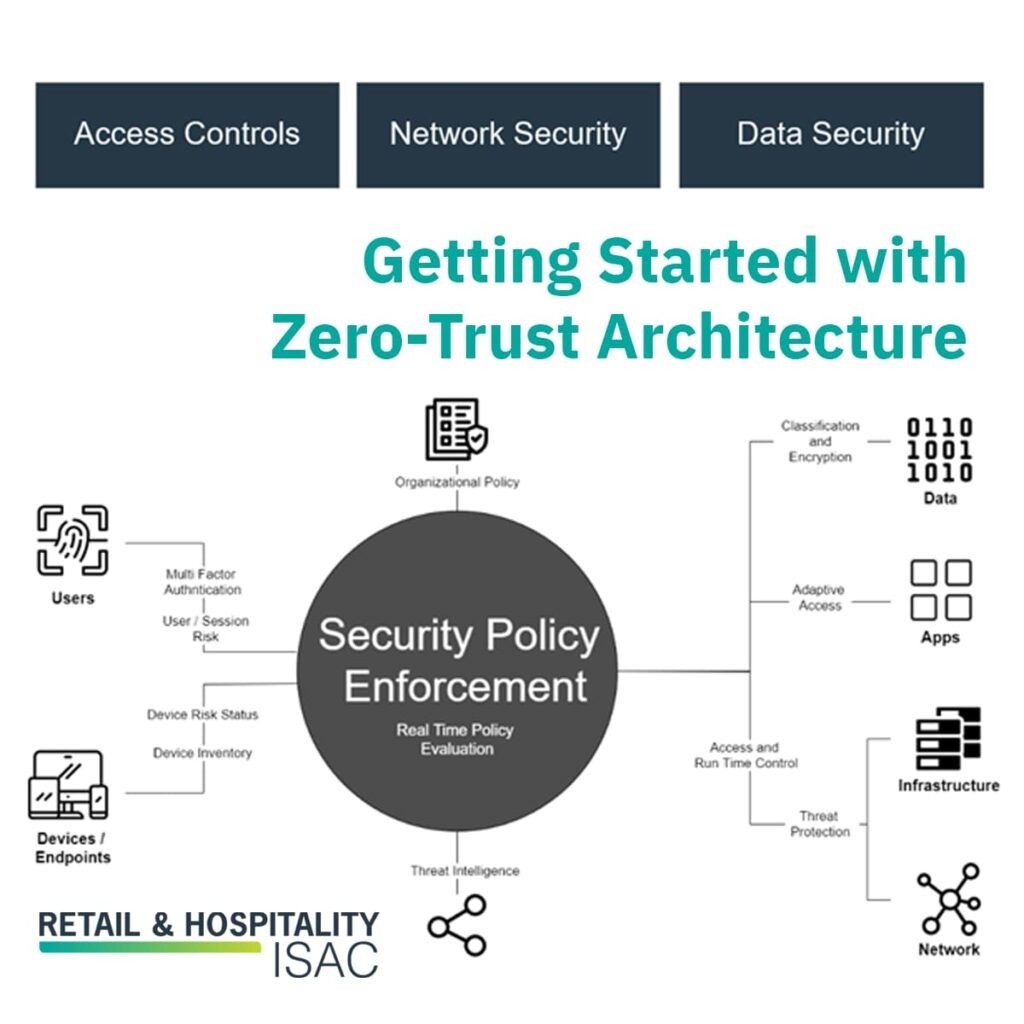
https://www.sans.org/blog/what-is-zero-trust-architecture
Zero Trust Architecture ZTA is a security model based on the principle of least privilege Least privilege means that users and devices are only granted the permissions they need to perform their tasks

https://www.crowdstrike.com/cybersecurity-101/zero-trust-security
What are the Core Principles of the Zero Trust Model The Zero Trust model based on NIST 800 207 includes the following core principles Continuous verification Always verify access all the time for all resources Limit the blast radius Minimize impact if an external or insider breach occurs Automate context collection and response

Zero Trust Model Of Information Security Principles Of Trust Architecture

Forrester Zero Trust Model Images And Photos Finder

How To Think About Zero Trust Architectures On AWS AWS Public Sector Blog

Zero Trust Architecture What It Is And What I Think Of It Tristan

Why You Need 6 Layers Of Zero Trust Control
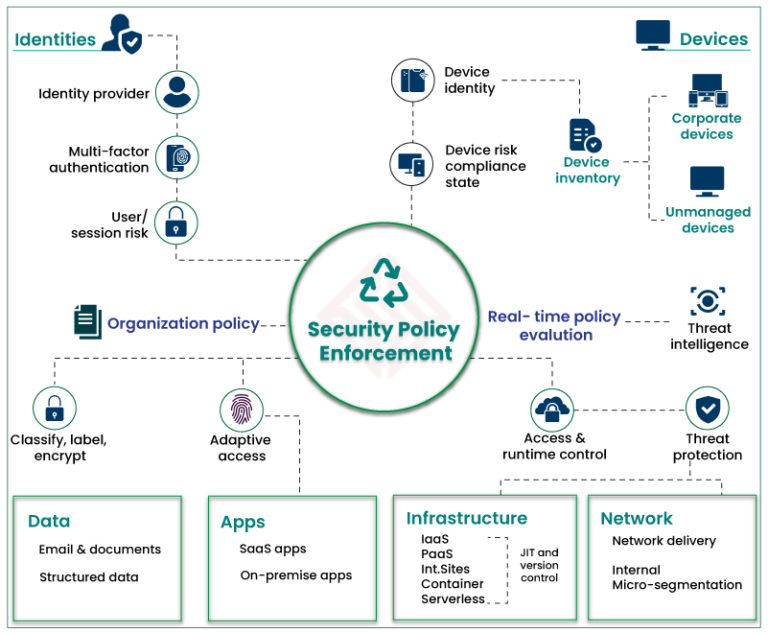
Zero Trust Security All You Need To Know

Zero Trust Security All You Need To Know
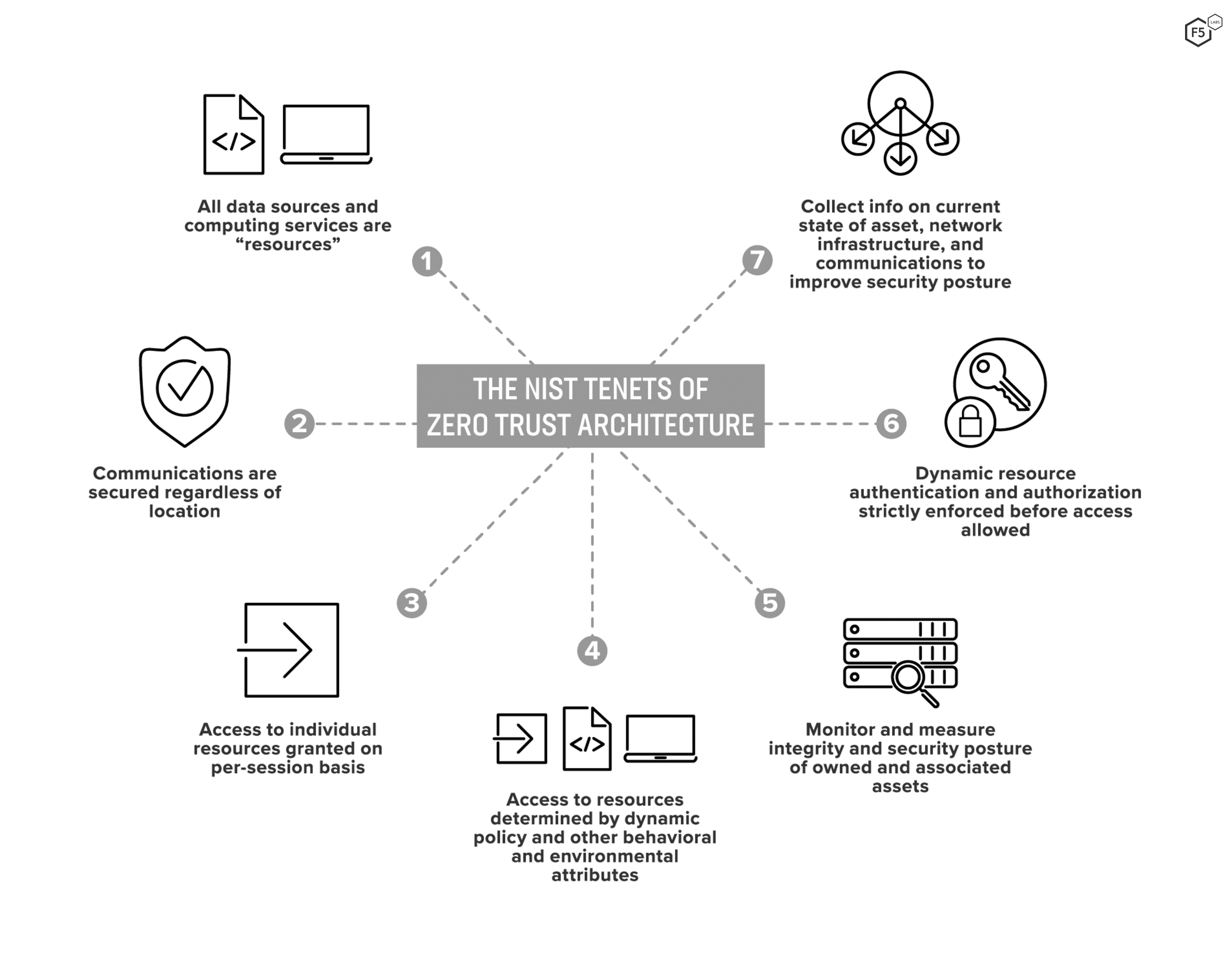
What Is Zero Trust Architecture ZTA F5 Labs
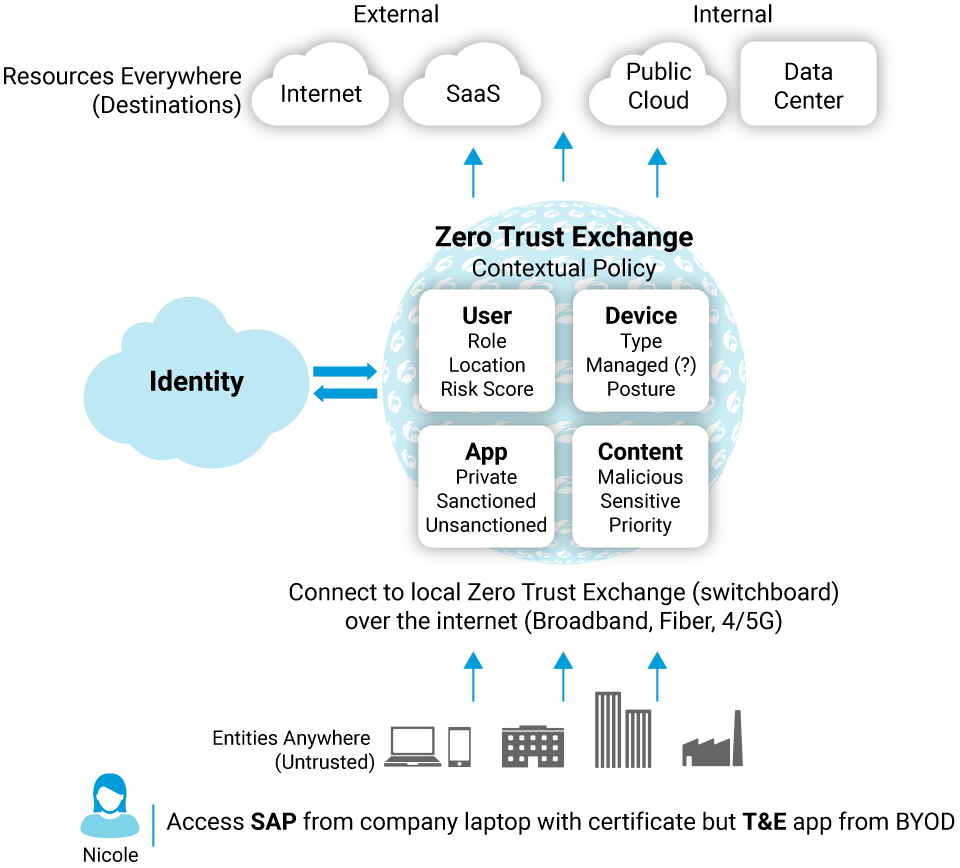
What Is Zero Trust Top Benefits How It Works Zscaler
Modelo De Seguridad Zero Trust Architecture Lisa News My XXX Hot Girl
What Is Zero Trust Architecture - Zero trust requires planning and executing across a broad range of functional areas including identity and access policies security solutions and workflows automation operations and network infrastructure Many organizations follow specific zero trust frameworks to build zero trust architectures