What Is Zero Trust Network Access As a zero trust subset ZTNA a Gartner coined term implements the concept of zero trust in the control of access to enterprise resources at the network level It hides the network location IP address and uses identity
Learn about Zero Trust Network Access ZTNA and its role in modern cybersecurity Explore how it secures remote access with strict verification Zero Trust Network Access ZTNA is swiftly becoming the standard for modern network security By continuously verifying user identities and applying least privilege access
What Is Zero Trust Network Access

What Is Zero Trust Network Access
https://cdn.thenewstack.io/media/2022/05/a202dee6-zero-trust-network-access-scaled.jpg

What Is Zero Trust Network Access
https://www.kappadata.nl/wp-content/uploads/2021/12/Zero-Trust-Network-Access-01-scaled.jpg

What Is Zero Trust Security Why You May Need It FAQ
https://integricom.net/wp-content/uploads/2022/10/Zero-Trust-Security-Model-168834811_m-scaled.jpeg
Zero Trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network regardless of whether they are sitting within or outside of the network perimeter Zero trust network access ZTNA also known as the software defined perimeter SDP is a set of technologies and functionalities that enable secure access to internal applications for remote users
Zero Trust network access ZTNA is an IT technology solution that requires all users to be authenticated continuously validated for security configuration accessing to Zero trust is a security strategy for modern multicloud networks Instead of focusing on the network perimeter a zero trust security model enforces security policies for each individual connection between users devices
Download What Is Zero Trust Network Access
More picture related to What Is Zero Trust Network Access
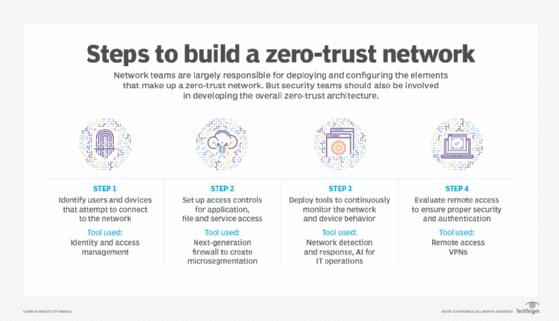
Zero Trust Vs Defense In Depth What Are The Differences News ITN
https://cdn.ttgtmedia.com/rms/onlineImages/networking-build_a_zero_trust_network-f_mobile.png

What Is Zero trust GateKeeper Proximity Passwordless 2FA
https://gkaccess.com/wp-content/uploads/2022/02/zero-trust-scaled.jpg

What Is Zero Trust By Wentz Wu ISSAP ISSEP ISSMP CISSP CCSP CSSLP
https://i0.wp.com/wentzwu.com/wp-content/uploads/2020/10/Zero-Trust-Cybersecurity-Paradigm.jpg?w=4000&ssl=1
Zero trust network access ZTNA is an approach to enterprise IT security that provides secure remote access to a company s data applications networks and services based on defined access control policies Zero Trust Network Access ZTNA helps protect remote users by providing granular access controls that are tailored to the individual user or device This allows organizations to limit access to certain resources based on
Zero Trust Network Access ZTNA is a modern security model designed to provide safe and secure access to a company s network and resources Unlike traditional ZTNA Zero Trust Network Access is a security model focused on verifying every user and device before granting access to corporate applications aiming to ensure secure

What Is Zero Trust Security Architecture F5
https://www.f5.com/content/dam/f5-com/page-assets-en/home-en/resources/glossary/zero-trust-tenets.png
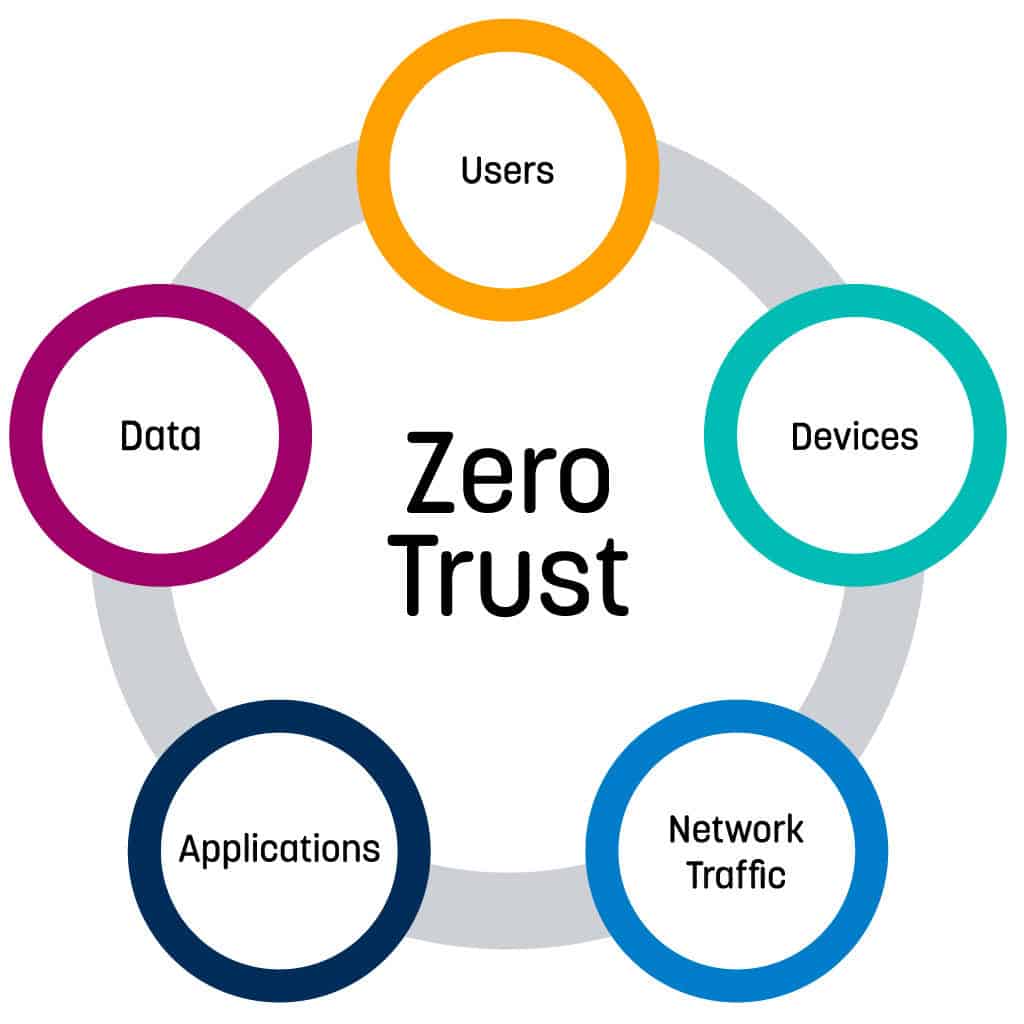
Microsoft Promoot Mindset Op Zero Trust beveiliging
https://logrhythm.com/wp-content/uploads/2021/03/R2_Zero_Trust_Graphic_Mar21_KMH_VG1595-1024x1024.jpg

https://www.techtarget.com › searchnetwor…
As a zero trust subset ZTNA a Gartner coined term implements the concept of zero trust in the control of access to enterprise resources at the network level It hides the network location IP address and uses identity

https://www.paloaltonetworks.com › cyberp…
Learn about Zero Trust Network Access ZTNA and its role in modern cybersecurity Explore how it secures remote access with strict verification
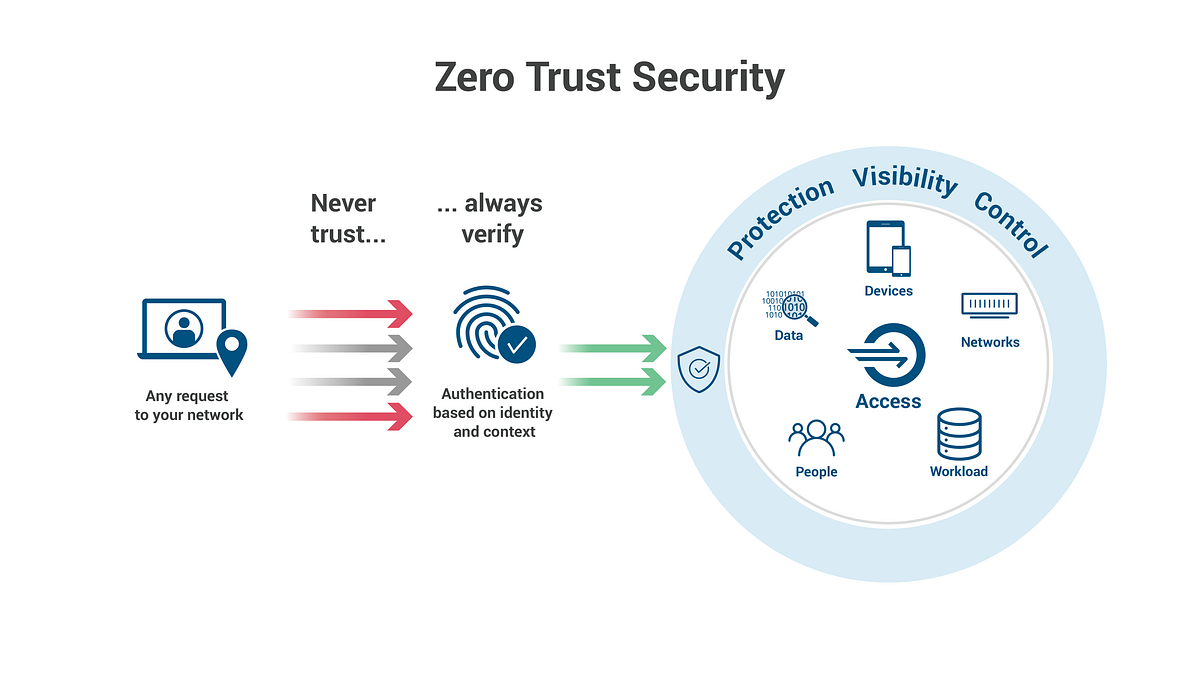
Zero Trust Network Access A Solution To Network Security By Noel

What Is Zero Trust Security Architecture F5
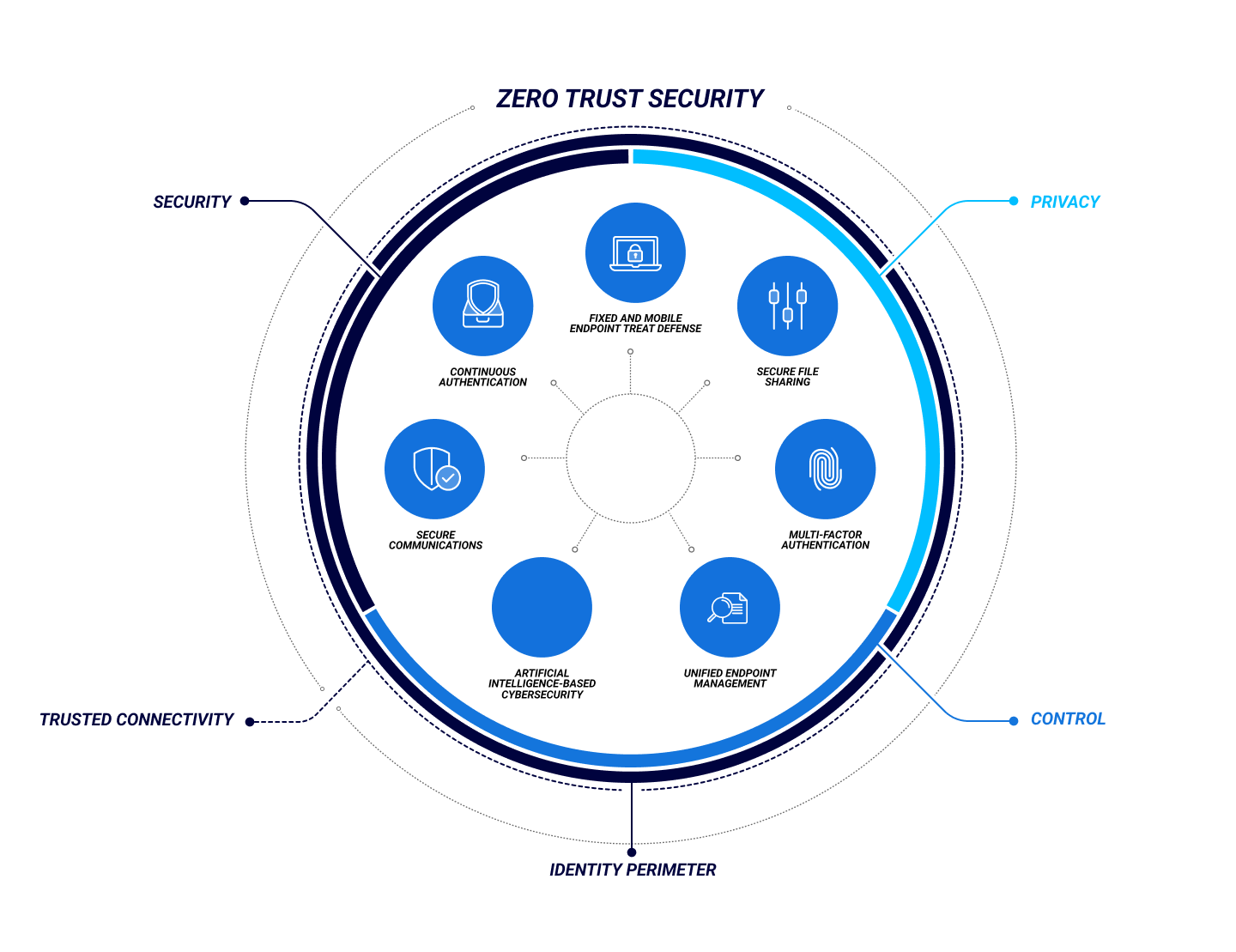
What Is Zero Trust Security
.png)
Never Trust Always Verify Zero Trust Architecture Skyflow
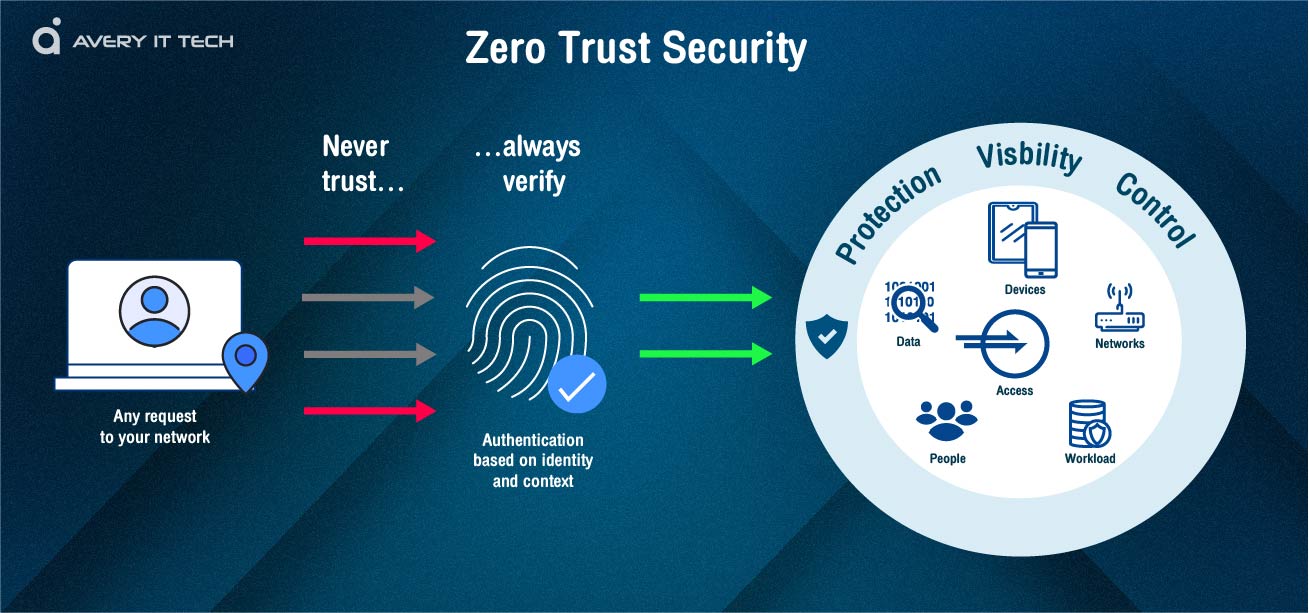
Zero Trust Network Access Concept Averyittech
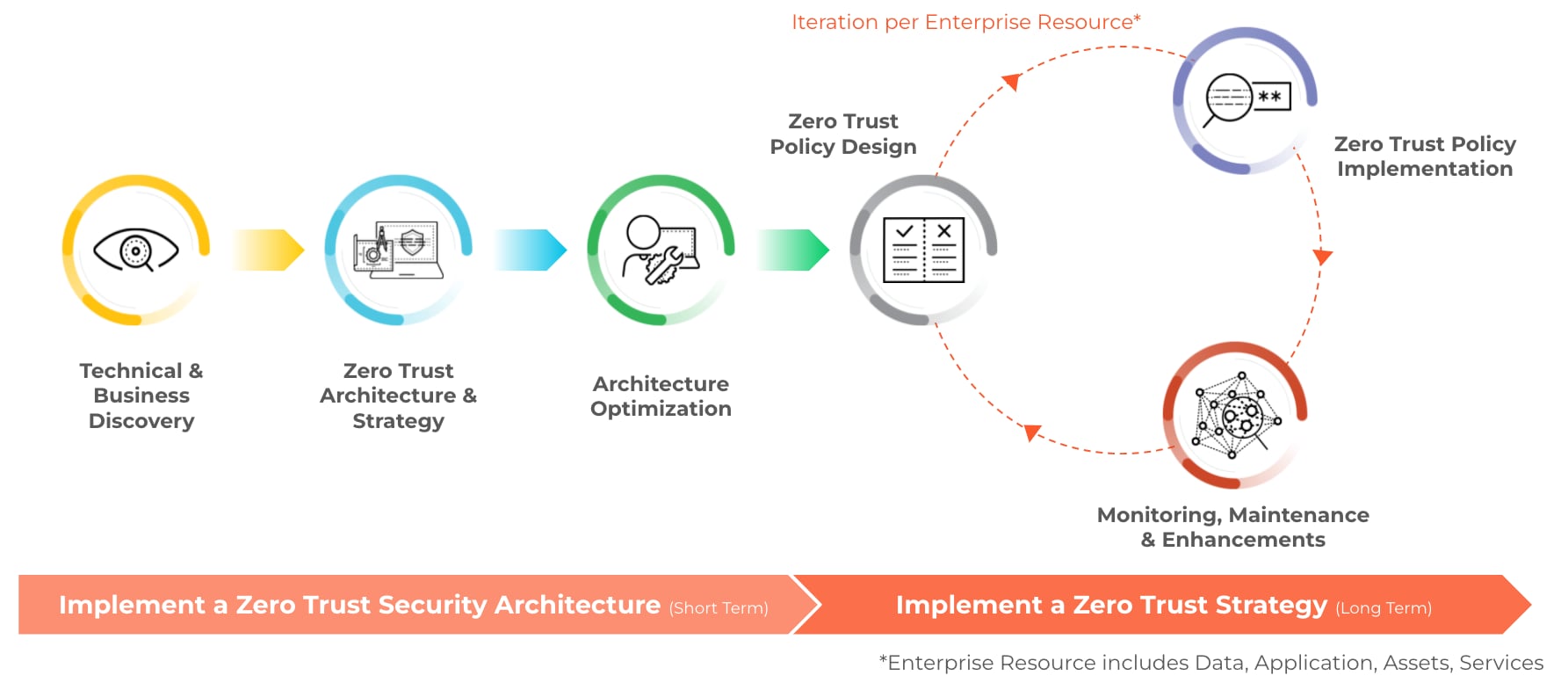
Strategy To Implementation With The Zero Trust Advisory Service Palo

Strategy To Implementation With The Zero Trust Advisory Service Palo
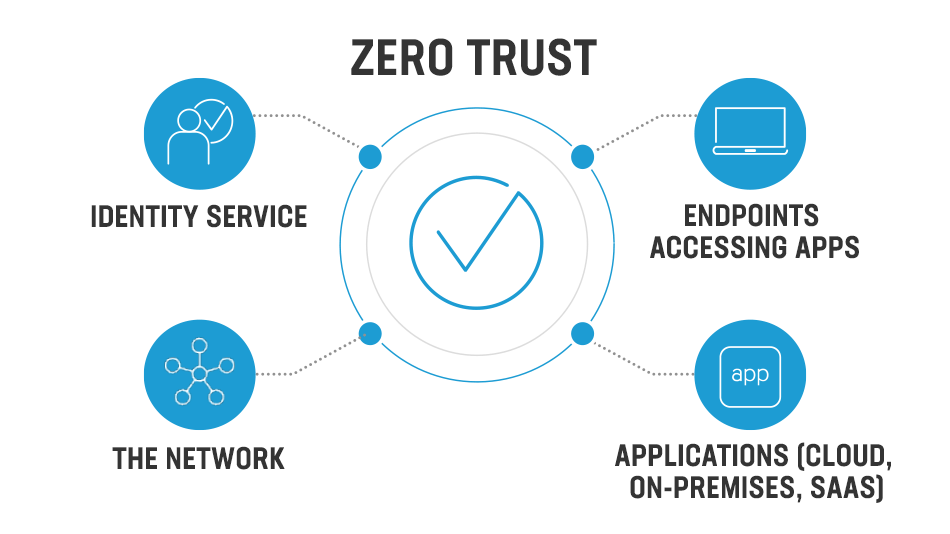
Making Zero Trust Real Vaultum City
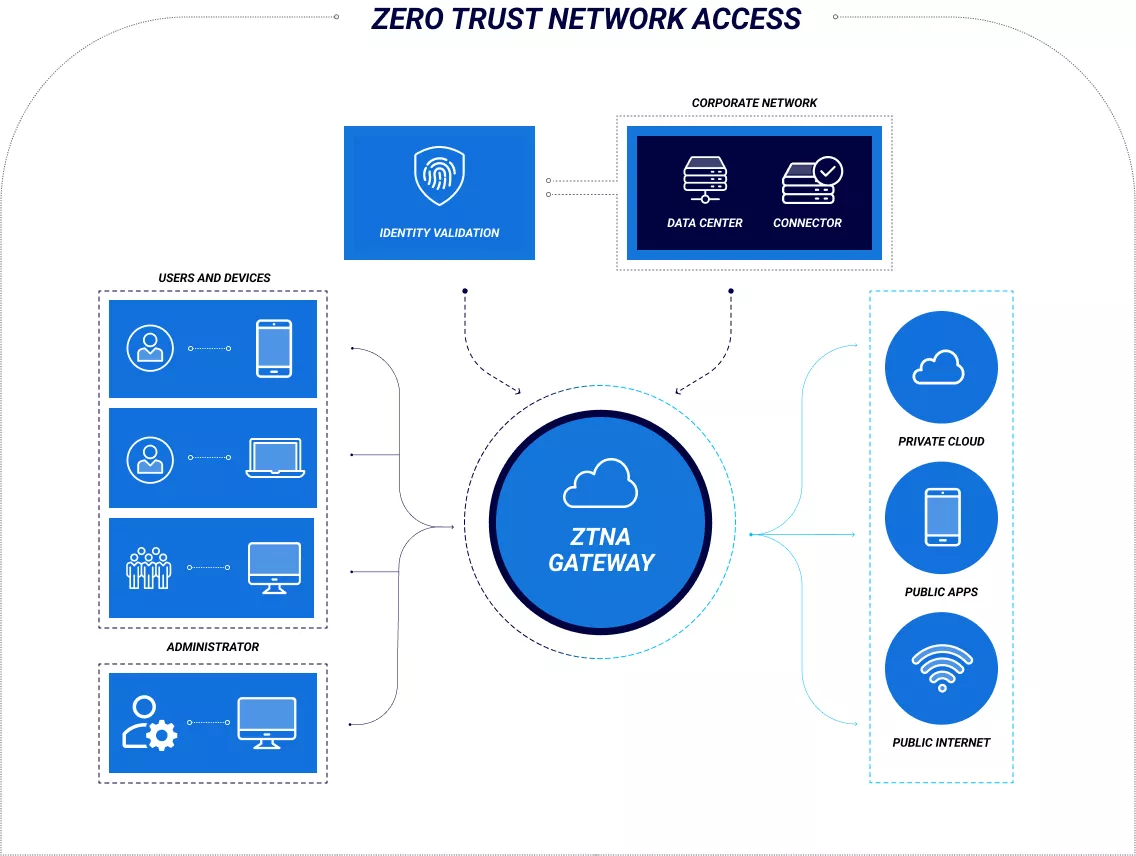
Zero Trust
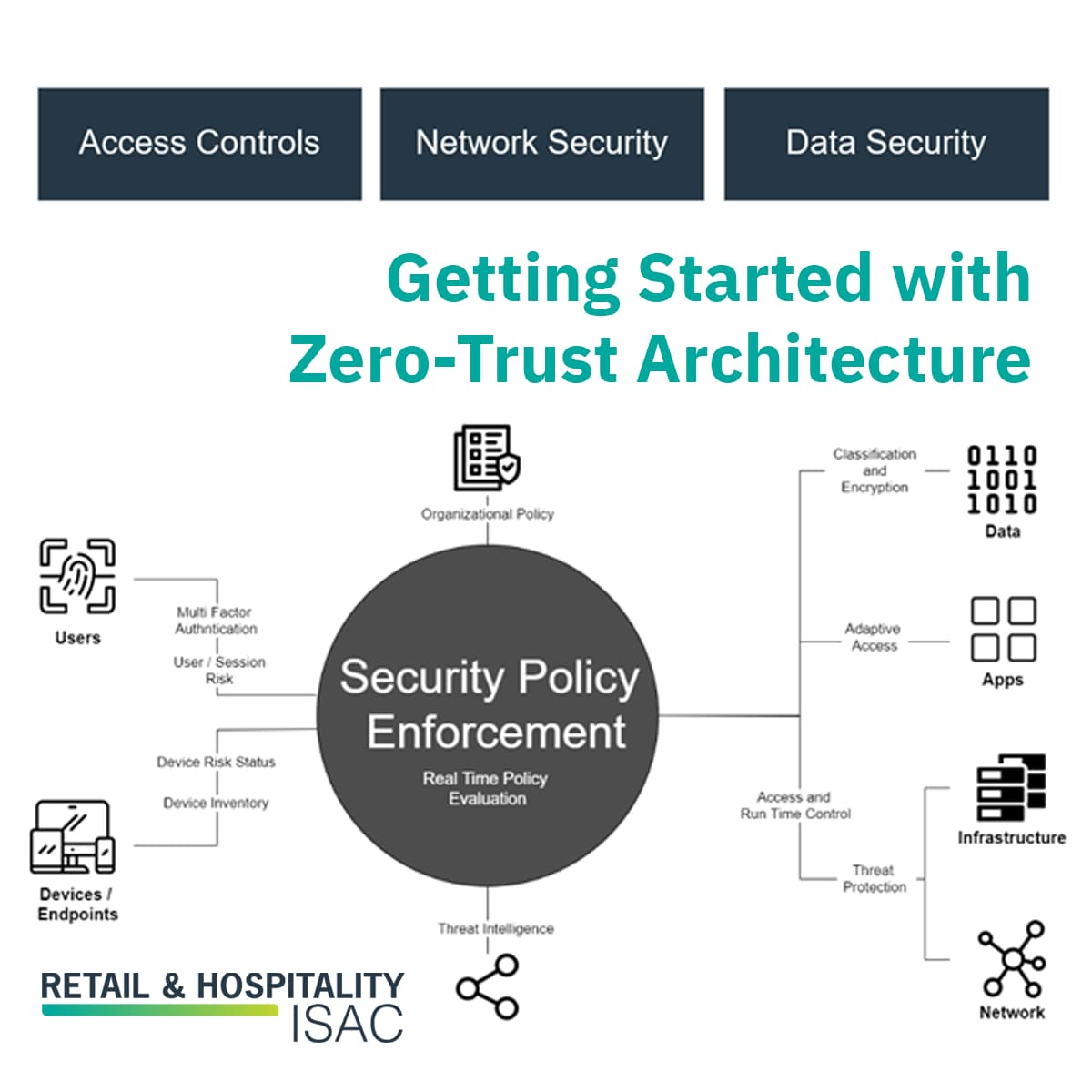
RH ISAC Zero Trust Architecture ZTA How To Get Started
What Is Zero Trust Network Access - Zero trust is a security strategy for modern multicloud networks Instead of focusing on the network perimeter a zero trust security model enforces security policies for each individual connection between users devices