Zero Trust Policy Definition Zero Trust is a security framework requiring all users whether in or outside the organization s network to be authenticated authorized and continuously validated for security configuration and posture before being granted or keeping access to applications and data
Zero Trust security means that no one is trusted by default from inside or outside the network and verification is required from everyone trying to gain access to resources on the network This added layer of security has been shown to prevent data breaches Studies have shown that the average cost of a single data breach is over 3 million Zero Trust is a security strategy It is not a product or a service but an approach in designing and implementing the following set of security principles Expand table Principle Description Verify explicitly Always authenticate and authorize based on all available data points Use least privilege access
Zero Trust Policy Definition
Zero Trust Policy Definition
https://miro.medium.com/max/1200/1*qOqrAbZAU9rsTh__oRPMdA.jpeg

Never Trust Always Verify Zero Trust Architecture Skyflow
https://assets-global.website-files.com/5fff1b18d19a56869649c806/61130401a3a05d34aa41ed97_Evis Zero Trust Blog OG.png
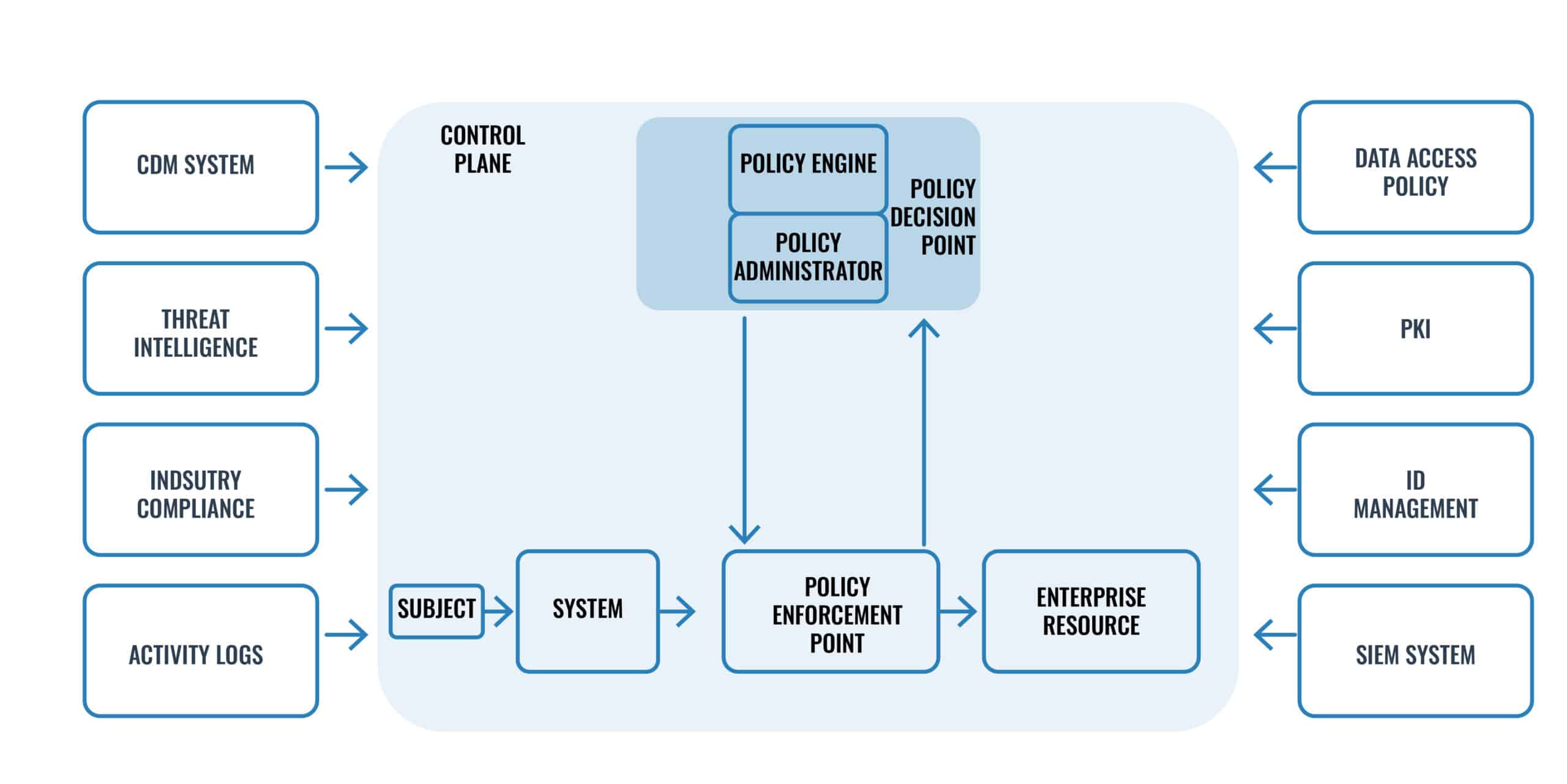
Zero Trust Architecture Explained A Step by Step Approach
https://cdn.comparitech.com/wp-content/uploads/2021/11/Policy-02-scaled.jpg
The main concept behind the zero trust security model is never trust always verify which means that users and devices should not be trusted by default even if they are connected to a permissioned network such as a corporate LAN and even if they were previously verified What is a Zero Trust Policy Organizations are rushing to implement zero trust principles and technology in their organization It is widely understood that zero trust can better protect a modern IT environment prevent cyber attacks and limit the damage caused by breaches when they occur
Zero trust is a modern security strategy based on the principle never trust always verify Instead of assuming everything behind the corporate firewall is safe the Zero Trust model assumes breach and verifies each request as though it originates from an open network Zero trust ZT is the term for an evolving set of cybersecurity paradigms that move defenses from static network based perimeters to focus on users assets and resources A zero trust architecture ZTA uses zero trust principles to plan industrial and enterprise infrastructure and workflows
Download Zero Trust Policy Definition
More picture related to Zero Trust Policy Definition
Zero Trust Security
https://media.licdn.com/dms/image/C5612AQEar4vXQ1YXsA/article-cover_image-shrink_720_1280/0/1619183187814?e=2147483647&v=beta&t=owOP4hVGOpg9NGXb52TXNyvHAm2SxiqkHTsF0XG-wqI

What Is Zero Trust Security CoreView
https://assets.website-files.com/612933c2d902f20aa8205a95/612eb1b3008785f5d21d1663_Microsoft-Solution-Zero-Trust.png

Facts About Zero Trust Modern Approach To Security
https://itsecuritywire.com/wp-content/uploads/2022/04/Facts-about-Zero-Trust-Modern-Approach-to-Security.png
Zero trust is a cloud security model designed to secure modern organizations by removing implicit trust and enforcing strict identity authentication and The principles of Zero Trust are Verify explicitly Consider every data point before authenticating someone s access including their identity location and device as well as how the resource is classified and if there s anything unusual that might be a red flag Use least privileged access
[desc-10] [desc-11]

Zero Trust Mythbuster Why Identity And Access Management Still Matter
https://i.nextmedia.com.au/Videos/Zero_Trust.png

Contractionary Monetary Policy Definition Objectives Example
https://static.seekingalpha.com/cdn/s3/uploads/getty_images/1366685616/image_1366685616.jpg?io=getty-c-w1280

https://www.crowdstrike.com/cybersecurity-101/zero-trust-security
Zero Trust is a security framework requiring all users whether in or outside the organization s network to be authenticated authorized and continuously validated for security configuration and posture before being granted or keeping access to applications and data

https://www.cloudflare.com/.../what-is-zero-trust
Zero Trust security means that no one is trusted by default from inside or outside the network and verification is required from everyone trying to gain access to resources on the network This added layer of security has been shown to prevent data breaches Studies have shown that the average cost of a single data breach is over 3 million

Zero Trust Atlassian Cloud Dmove Blog

Zero Trust Mythbuster Why Identity And Access Management Still Matter

What Is Zero Trust Policy How It Impacts The Organisational Culture

Why You Need 6 Layers Of Zero Trust Control
Microsoft Promoot Mindset Op Zero Trust beveiliging

Why A Zero Trust Security Policy Is Popular Peak I T

Why A Zero Trust Security Policy Is Popular Peak I T
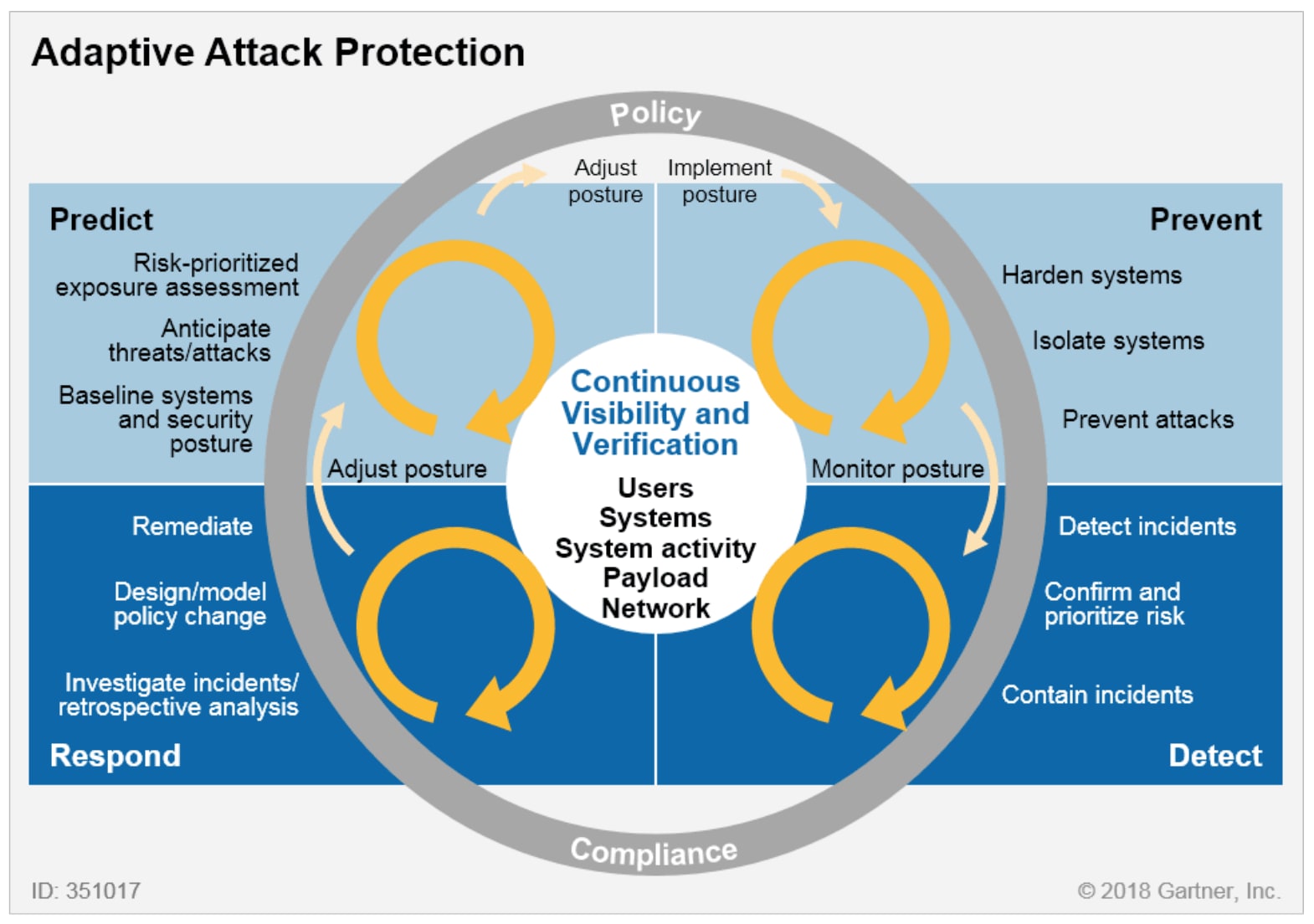
The Gartner CARTA Model

Three Fundamentals To A Successful Zero Trust Rollout
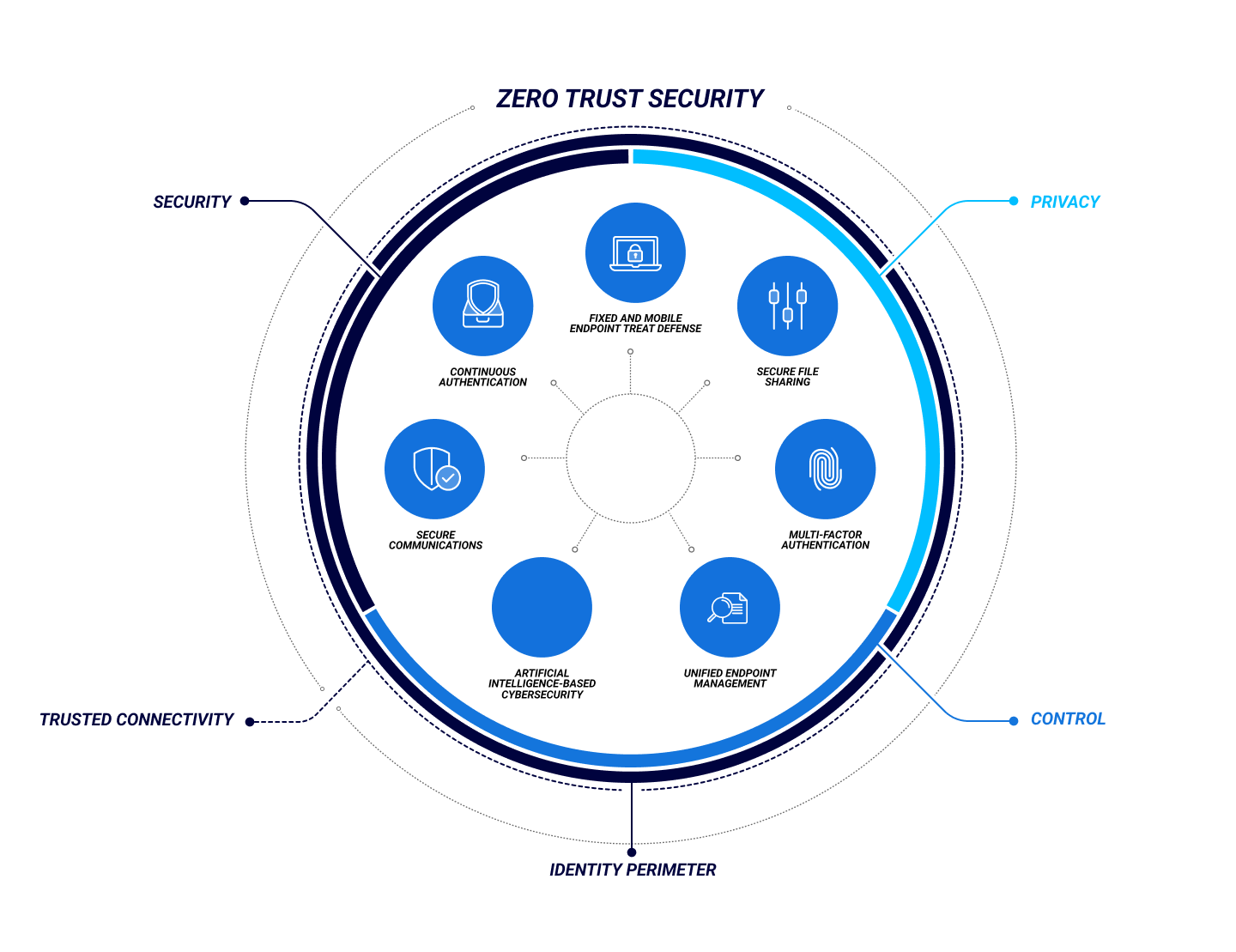
What Is Zero Trust Security
Zero Trust Policy Definition - [desc-14]
