Zero Trust Strategy Example Example 1 Google s BeyondCorp Initiative These examples illustrate how various organizations are successfully implementing Zero Trust strategies tailored to their unique
In this article we have presented a zero trust architecture example to illustrate how a fully secured organization operates and included 12 additional zero trust examples What are the Core Principles of the Zero Trust Model Here are the main principles driving zero trust implementations at organizations Strict Evaluation of Access Controls The zero trust model assumes that potential attackers may
Zero Trust Strategy Example

Zero Trust Strategy Example
https://integricom.net/wp-content/uploads/2022/10/Zero-Trust-Security-Model-168834811_m-scaled.jpeg

A Peek Into The Newly Released DoD Zero Trust Strategy Part 1 Of Two
https://storage.googleapis.com/blogs-images/ciscoblogs/1/2022/11/Feature.jpg
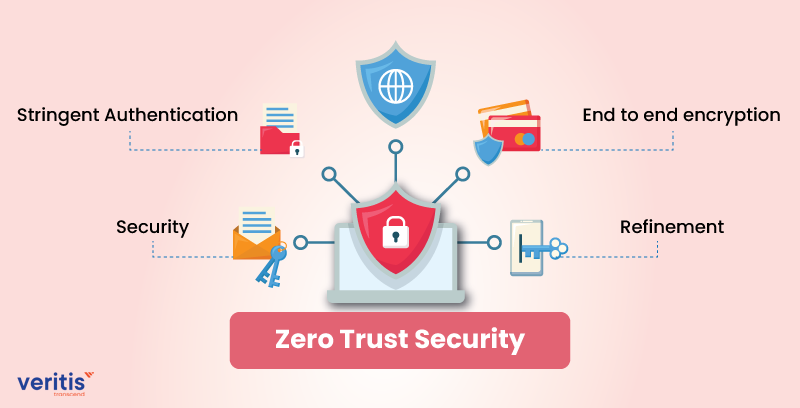
Zero Trust Strategy The Modern Security Solution For Cloud Computing
https://veritis.com/wp-content/uploads/2021/08/zero-trust-strategy.png
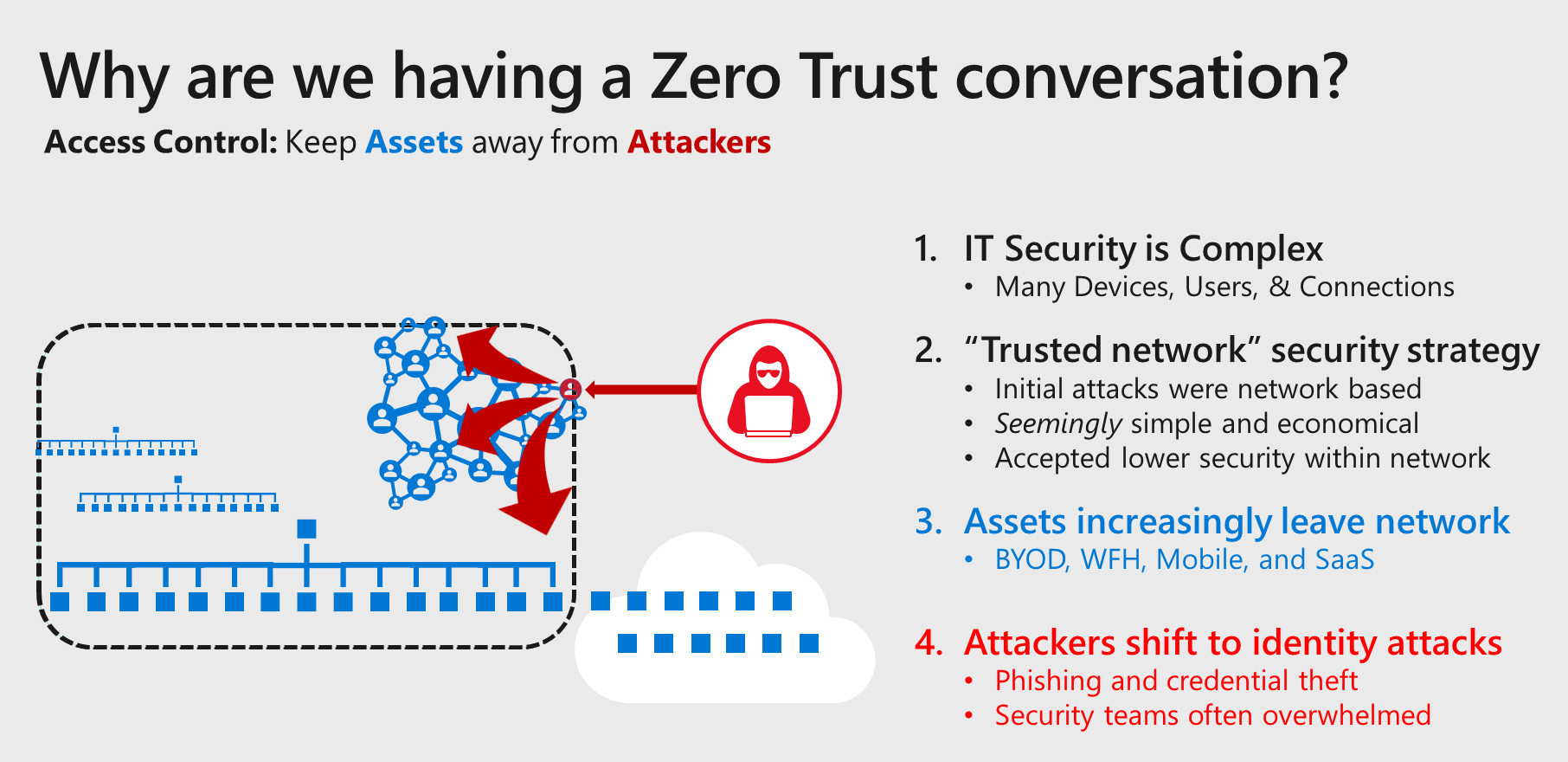
The Zero Trust framework is widely regarded as a key security model and a commonly referenced standard in modern cybersecurity Unlike legacy perimeter based models Zero Trust assumes that adversaries will Implementing a Zero Trust Architecture can be done in steps without disrupting employee productivity and connectivity This roadmap was built by security experts to provide a vendor agnostic Zero Trust architecture and example
Zero Trust is a modern security strategy based on the principle never trust always verify Instead of assuming everything behind the corporate firewall is safe the Zero Trust model assumes Zero Trust is a new security model that assumes breach and verifies each request as though it originated from an uncontrolled network In this article you ll learn about the guiding principles of Zero Trust and find
Download Zero Trust Strategy Example
More picture related to Zero Trust Strategy Example
Zero Trust Strategy what Good Looks Like ThreatsHub Cybersecurity News
https://www.threatshub.org/blog/coredata/uploads/2019/11/zero-trust-strategy-what-good-looks-like.png

DoD Zero Trust Strategy Industrial Cyber
https://industrialcyber.co/wp-content/uploads/2022/11/2022.11.24-New-DoD-zero-trust-strategy-to-reduce-attack-surface-while-enabling-risk-management-and-effective-data-sharing-.jpg

The Zero Trust Strategy Greylock
https://greylock.com/wp-content/uploads/2021/10/Twitter-Yoast-IMG-The-Zero-Trust-Strategy.png
Understand the Zero Trust security model learn about the principles and apply the Zero Trust architecture using Microsoft 365 and Microsoft Azure services Improve security with a Zero Trust access model Microsoft Corporate Vice President and CISO Bret Arsenault describes how Microsoft is approaching Zero Trust with advice for applying learnings to your organization
A Zero Trust strategy for cybersecurity provides the opportunity to create a more robust and resilient posture simplify security management improve end user experience and enable The zero trust approach enables you to solve common security issues such as safeguarding remote workers protecting hybrid cloud infrastructure and defending against costly and
Free Resources To Begin Your Zero Trust Implementation LogRhythm
https://logrhythm.com/wp-content/uploads/2021/05/Zero-Trust-Resource-Mockup.png
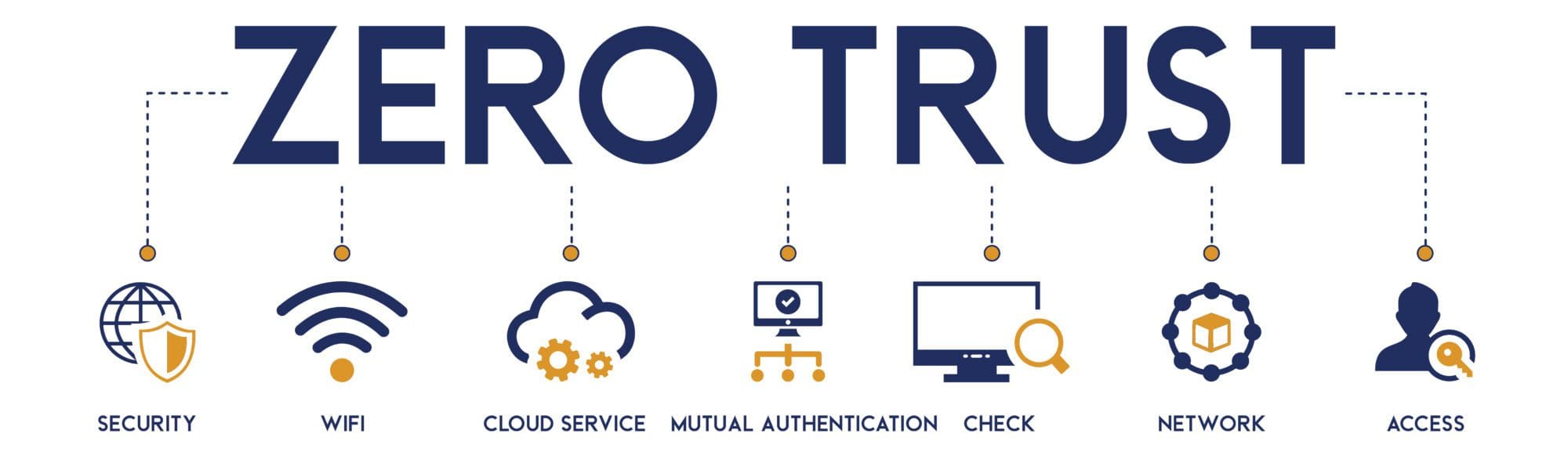
Zero Trust Security Zero Trust Network ImageQuest Blog
https://www.imagequest.com/wp-content/uploads/2023/01/AdobeStock_497719035-2000x600.jpeg

https://www.consumersearch.com › technology › real...
Example 1 Google s BeyondCorp Initiative These examples illustrate how various organizations are successfully implementing Zero Trust strategies tailored to their unique

https://www.pomerium.com › blog › zero-trust...
In this article we have presented a zero trust architecture example to illustrate how a fully secured organization operates and included 12 additional zero trust examples

Strengthen Your Zero Trust Strategy With SailPoint And Ping Identity

Free Resources To Begin Your Zero Trust Implementation LogRhythm

The Evolution To Zero Trust And CMMC Implications

Never Trust Always Verify Zero Trust Architecture Skyflow
How To Build A Zero Trust Strategy CrowdStrike

Embracing Zero Trust Home

Embracing Zero Trust Home
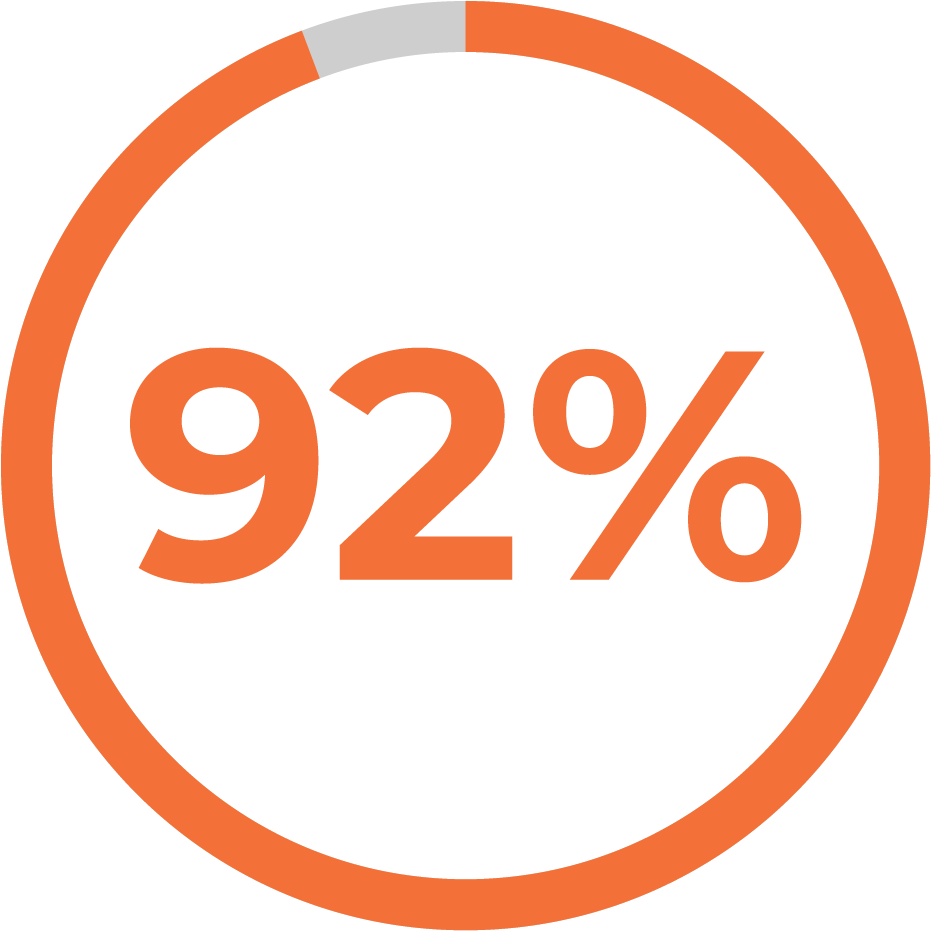
Enhance Your Cybersecurity With A Zero Trust Assessment Insentra

Zero Trust Mythbuster Why Identity And Access Management Still Matter

Facts About Zero Trust Modern Approach To Security
Zero Trust Strategy Example - Zero Trust Architecture or ZTA refers to the implementation practical application and design that enforces Zero Trust principles in an organization s IT infrastructure It provides the technical