What Is Root Of Trust A RoT is an essential foundational security component that provides a set of trustworthy functions that the rest of the device or system can use to establish strong levels of security Often integrated as a chip using a RoT gives devices a trusted source that can be relied upon within any cryptographic system
Everything you need to know about hardware root of trust simply explained in our primer What is a hardware root of trust Types Benefits Features and more Roots of trust are highly reliable hardware firmware and software components that perform specific critical security functions Because roots of trust are inherently trusted they must be secure by design
What Is Root Of Trust

What Is Root Of Trust
https://cpl.thalesgroup.com/themes/thalesesecurity/templates/dist/images/bg-intro-faq.jpg

Building A Hardware Root Of Trust
https://www.epsprogramming.com/blog/images/root-of-trust-banner.png
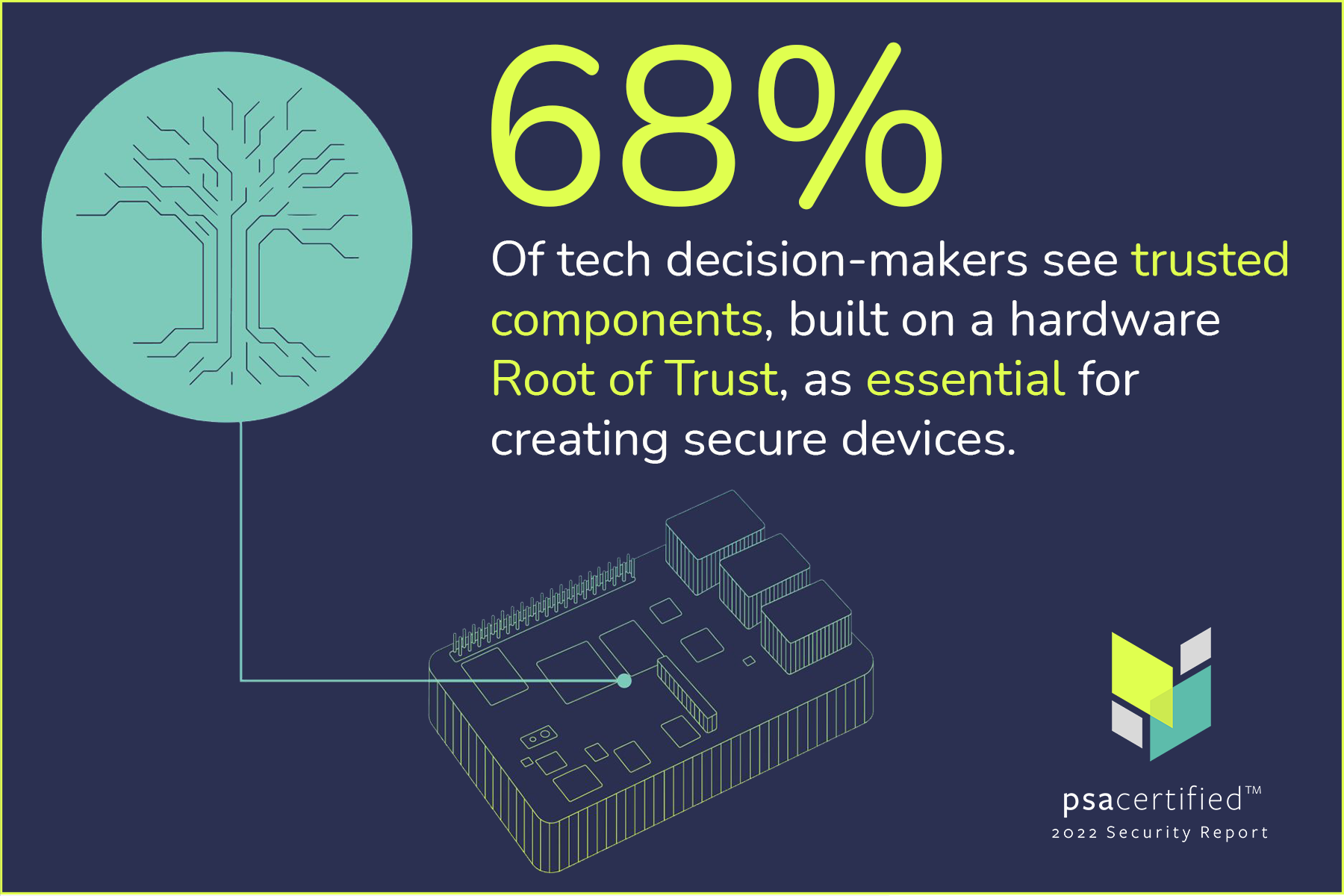
Unlocking The Value Of A Root Of Trust For OEMs PSA Certified
https://www.psacertified.org/app/uploads/2022/03/Trusted_components.png
A Root of Trust RoT is a trusted source within a cryptographic system essential for securing keys and performing critical operations like encryption and digital signature validation Typically embedded as a hardware security module HSM RoT ensures the integrity and security of cryptographic processes Root of Trust RoT is a source that can always be trusted within a cryptographic system Because cryptographic security is dependent on keys to encrypt and decrypt data and perform functions such as generating digital signatures and verifying signatures RoT schemes generally include a hardened hardware module
In Secured core PCs Windows Defender System Guard Secure Launch protects bootup with a technology known as the Dynamic Root of Trust for Measurement DRTM With DRTM the system initially follows the normal UEFI Secure Boot process A root of trust such as a hardware security key offers a physical and cryptographic guarantee of possession of a unique hardware device The private key material or secret cannot be extracted as the external authenticator cannot be cloned or tampered with and the privacy secrets cannot be revealed
Download What Is Root Of Trust
More picture related to What Is Root Of Trust

Cloud Foundation
https://docs.oracle.com/en/cloud/foundation/cloud_architecture/security/images/root-of-trust.png#fullpic

5 Elements To Secure Embedded System Part 2 Root of Trust RoT
https://beningo-embedded-group.s3.amazonaws.com/2021/08/Screen-Shot-2021-08-21-at-1.28.06-PM-2048x629.png

Root Of Trust
https://www.omertadigital.com/Images/building trust.png
Roots of Trust are highly reliable hardware firmware and software components that perform specific critical security functions They are building blocks upon which other components can derive secure functions Since roots of trust are inherently trusted they must be secure by design Roots of trust are highly reliable hardware firmware and software components that perform specific critical security functions Because roots of trust are inherently trusted they must be secure by design
Learn about the Root of Trust the role it plays in IoT and how the PSA Root of Trust PSA RoT provides security without the complexity Root of trust This is a shared immutable piece of information such as a private key from a chip manufacturer where the public key is known which is used to validate the whole chain of trust This is a single point of failure for the whole scheme
![]()
HPE Silicon Root Of Trust Brainstorm Studio
https://www.brainstormstudio.com/wp-content/uploads/2021/09/HPE-Silicon-Root-of-Trust.jpg
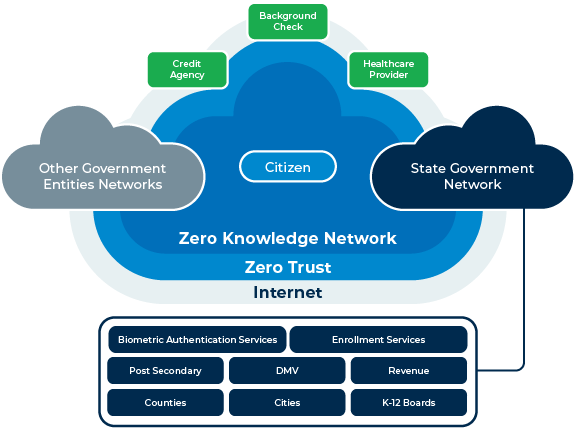
Identity As The Root Of Trust Journey
https://journeyid.com/wp-content/uploads/2020/10/Identity-as-the-Root-of-Trust-graphic.png

https://trustedcomputinggroup.org/about/what-is-a-root-of-trust-rot
A RoT is an essential foundational security component that provides a set of trustworthy functions that the rest of the device or system can use to establish strong levels of security Often integrated as a chip using a RoT gives devices a trusted source that can be relied upon within any cryptographic system

https://www.rambus.com/blogs/hardware-root-of-trust
Everything you need to know about hardware root of trust simply explained in our primer What is a hardware root of trust Types Benefits Features and more

What Is A Root Of Trust Yubico
HPE Silicon Root Of Trust Brainstorm Studio
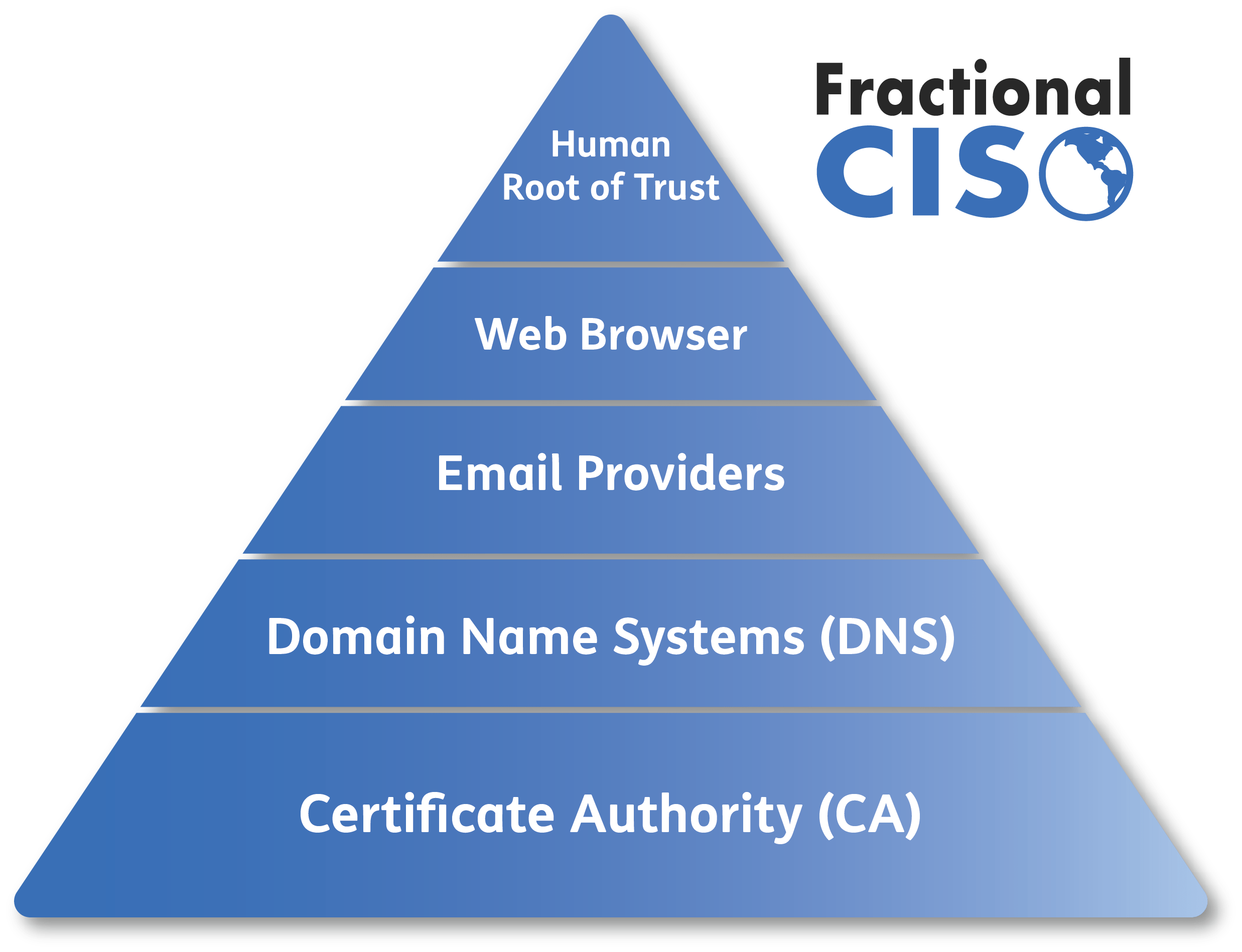
Human Root Of Trust Fractional CISO Virtual CISO

Secure Boot And Root Of Trust For Firmware Security

Building Trust Sean Heritage

Dynamic Root Of Trust And Challenges By Ijsptmjournal Issuu

Dynamic Root Of Trust And Challenges By Ijsptmjournal Issuu
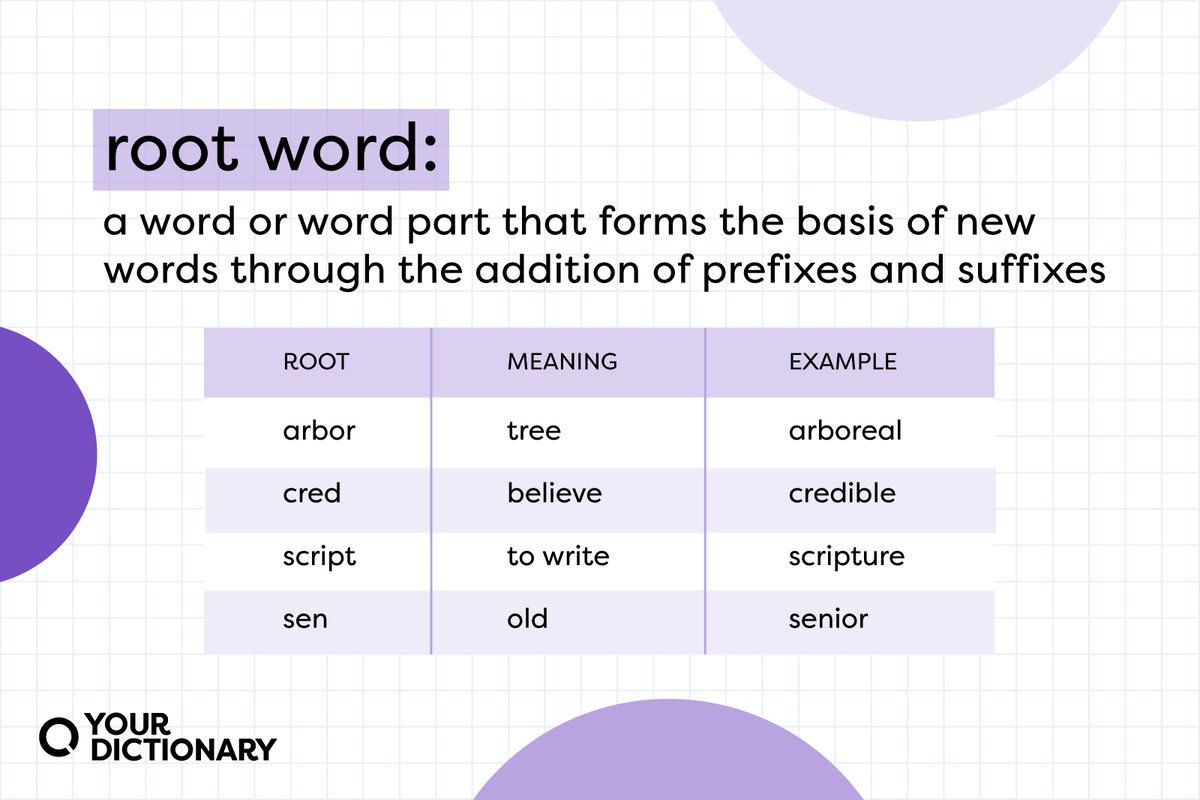
Examples Of Root Words 45 Common Roots With Meanings YourDictionary

Discretionary Trusts Should You Appoint A Corporate Or An Individual

Wills Vs Trusts What s The Difference Elder Law North Carolina
What Is Root Of Trust - In Secured core PCs Windows Defender System Guard Secure Launch protects bootup with a technology known as the Dynamic Root of Trust for Measurement DRTM With DRTM the system initially follows the normal UEFI Secure Boot process