Zero Trust Requirements Understand the Zero Trust security model learn about the principles and apply the Zero Trust architecture using Microsoft 365 and Microsoft Azure services
Zero trust ZT is the term for an evolving set of cybersecurity paradigms that move defenses from static network based perimeters to focus on users assets and resources A zero trust architecture ZTA uses zero trust principles to plan industrial and enterprise infrastructure and workflows A Zero Trust model provides security against ransomware and cybersecurity threats by assigning the least required access needed to perform specific tasks
Zero Trust Requirements

Zero Trust Requirements
https://www.f5.com/content/dam/f5-com/global-assets/resources-featurettes/reports-articles/zero-trust-in-an-application-centric-world_950x534.png
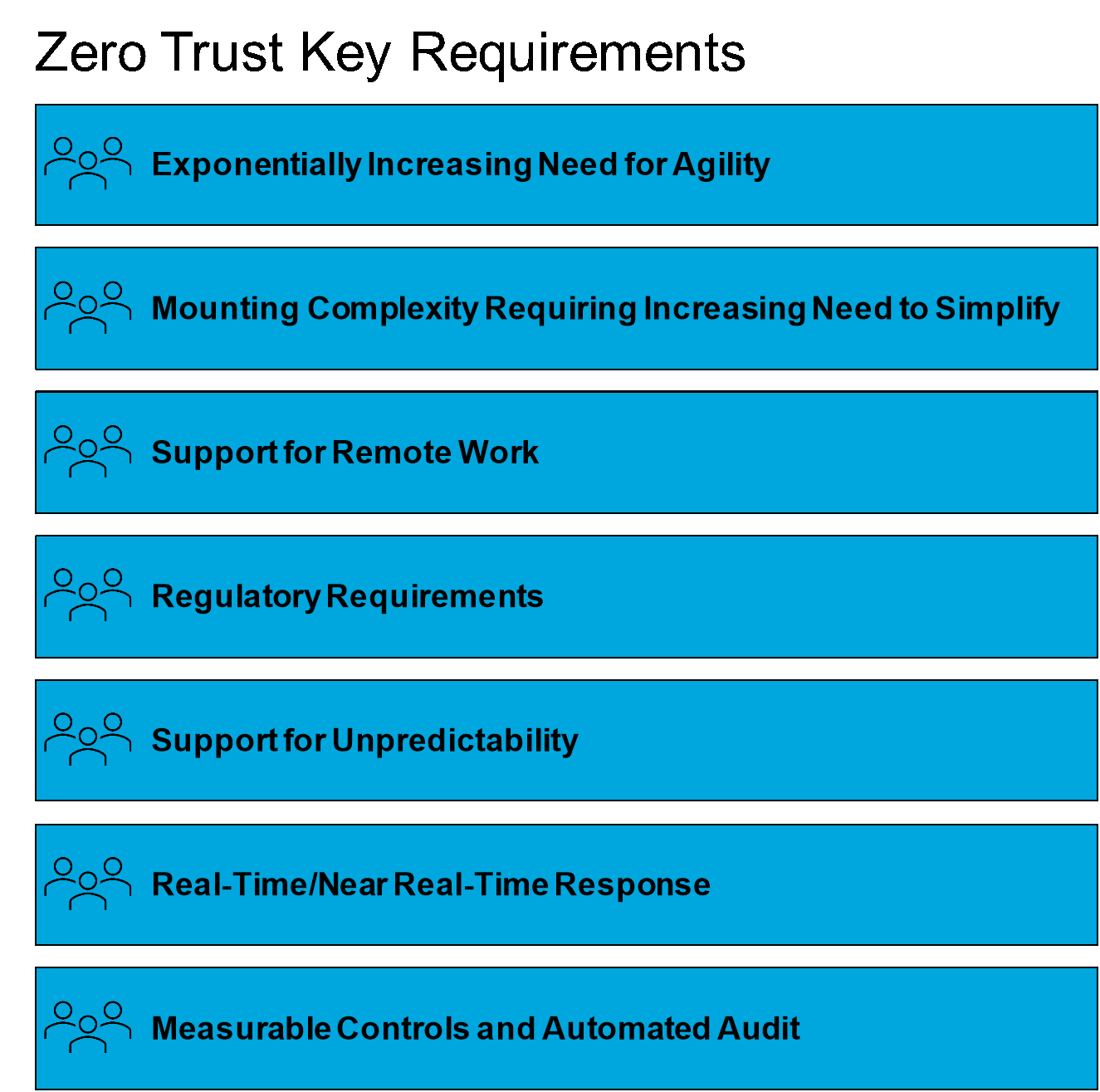
Zero Trust Core Principles
https://pubs.opengroup.org/security/zero-trust-principles/zero-trust-principles/zero-trust-principles.005.png
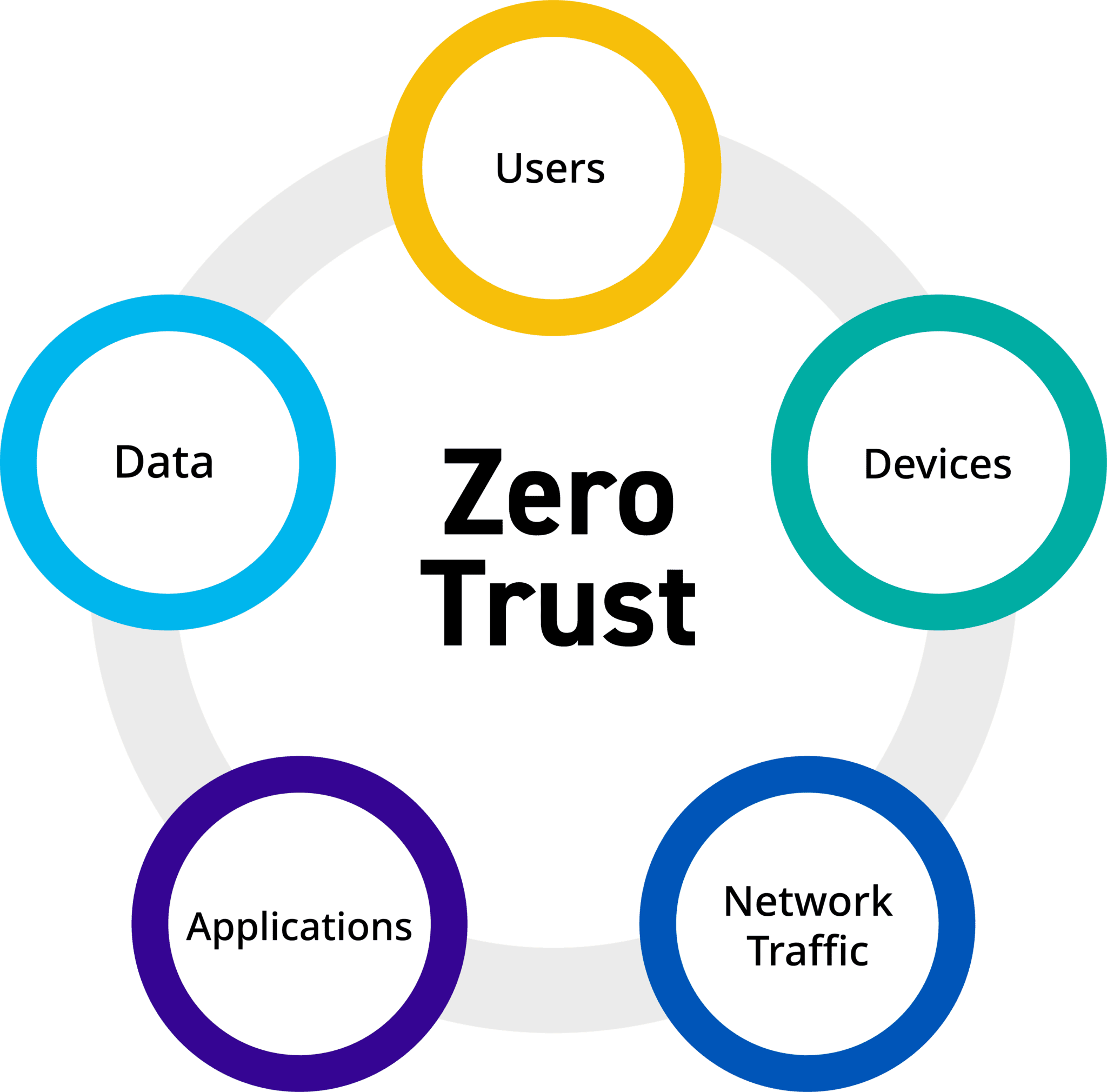
Embracing A Zero Trust Security Model
https://logrhythm.com/wp-content/uploads/2022/02/R1_Zero_Trust_Graphic_Feb22_JKE_VG1595-1-2048x2020.png
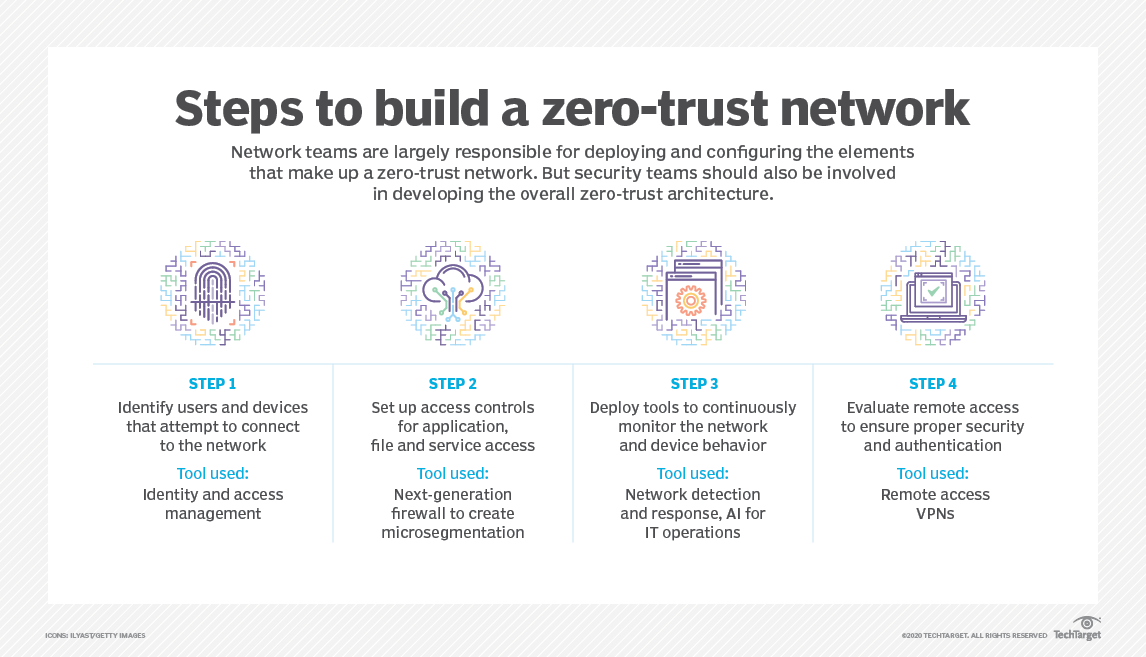
Zero trust requires planning and executing across a broad range of functional areas including identity and access policies security solutions and workflows automation operations and network infrastructure Many organizations follow specific zero trust frameworks to Zero Trust requires strong authentication of user identity application of least privilege policies and verification of user integrity Apply Zero Trust to applications removes implicit trust with various components of applications when they talk to each other
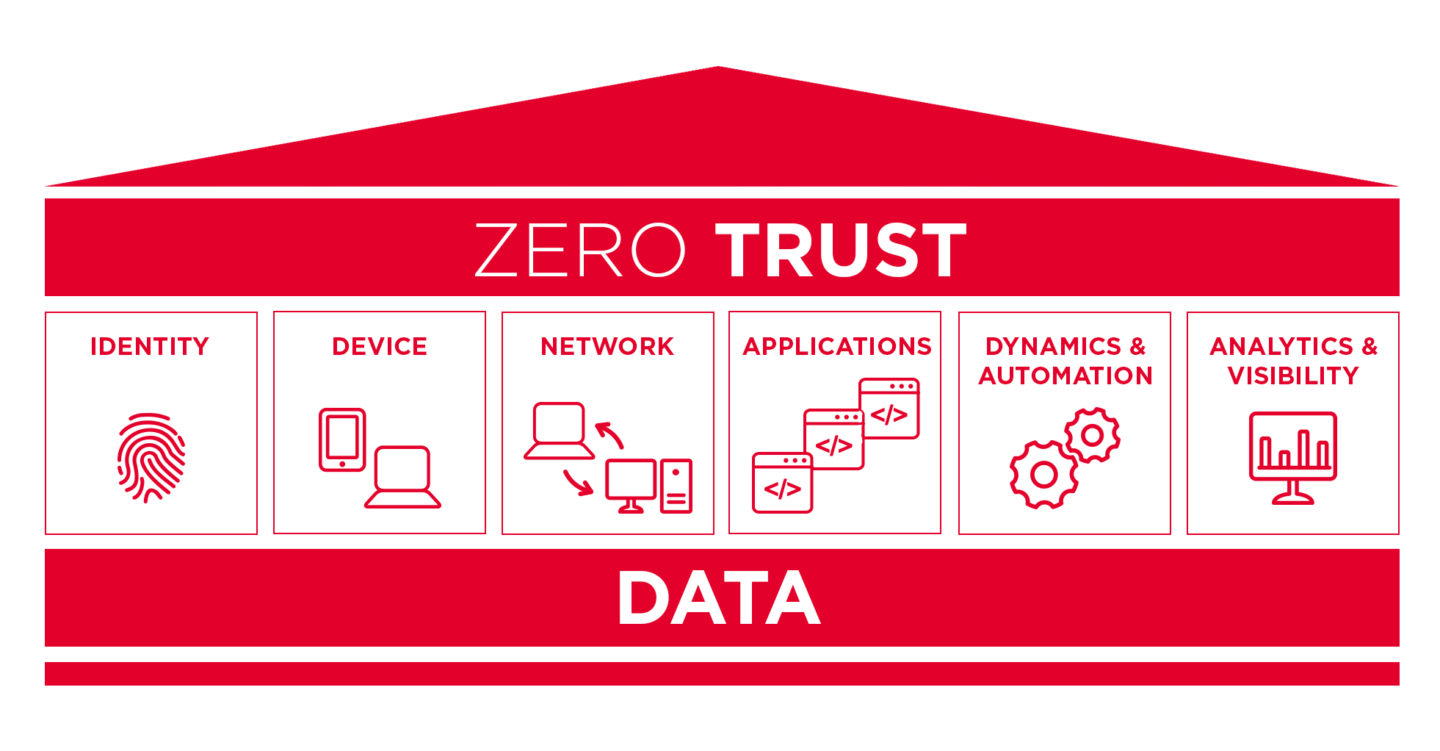
Zero Trust is a security framework requiring all users whether in or outside the organization s network to be authenticated authorized and continuously validated for security configuration and posture before being granted or keeping access to applications and data Abstract NIST Special Publication 800 207 defines zero trust as a set of cybersecurity principles used when planning and implementing an enterprise architecture These principles apply to endpoints services and data flows
Download Zero Trust Requirements
More picture related to Zero Trust Requirements
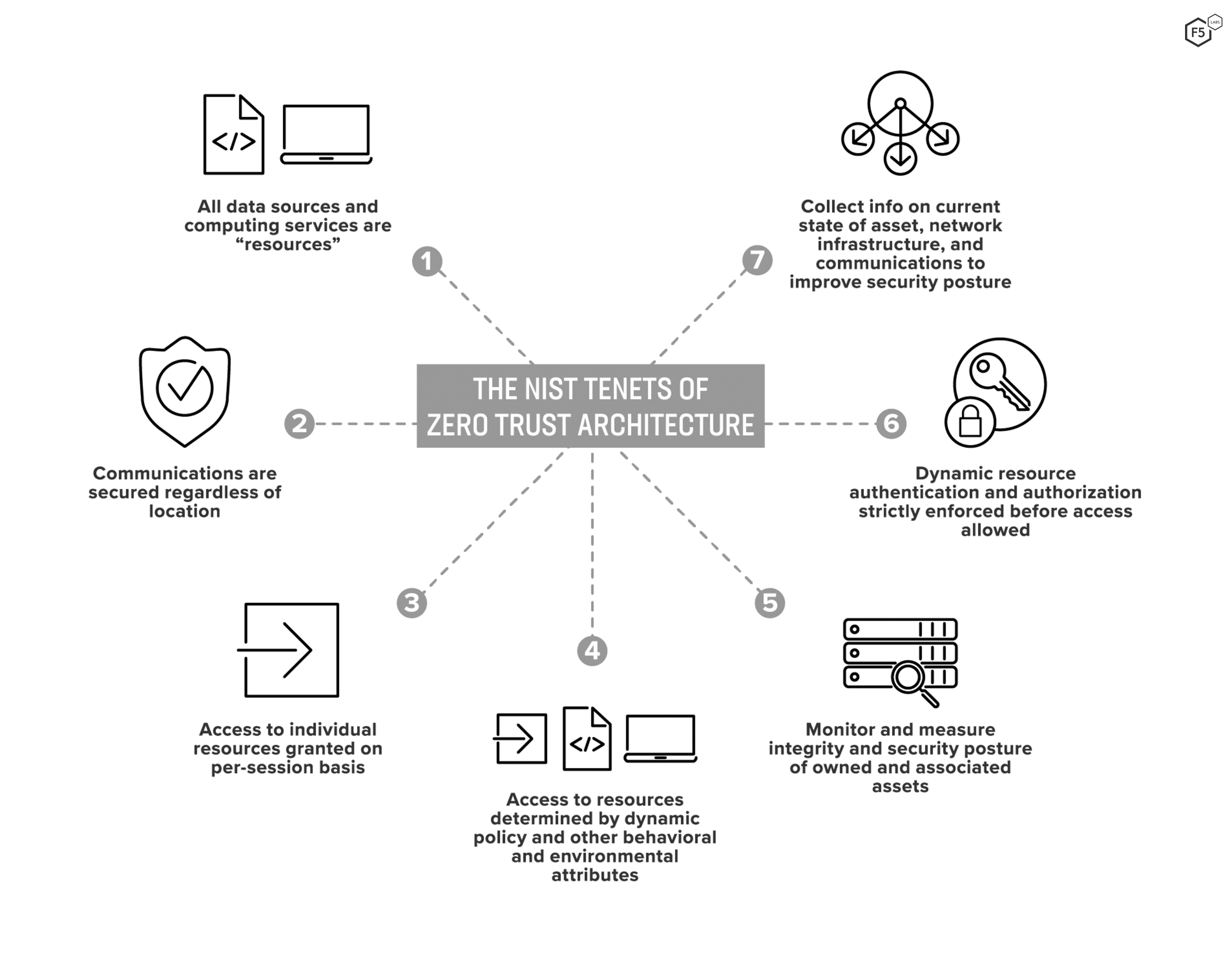
What Is Zero Trust Architecture ZTA F5 Labs
https://www.f5.com/content/dam/f5-labs-v2/article/articles/edu/20220705_what_is_zta/Fig1.png

Why You Need 6 Layers Of Zero Trust Control
https://questsys.com/wp-content/uploads/2021/05/Zero-Trust_Blog-Graphic_Final.jpg
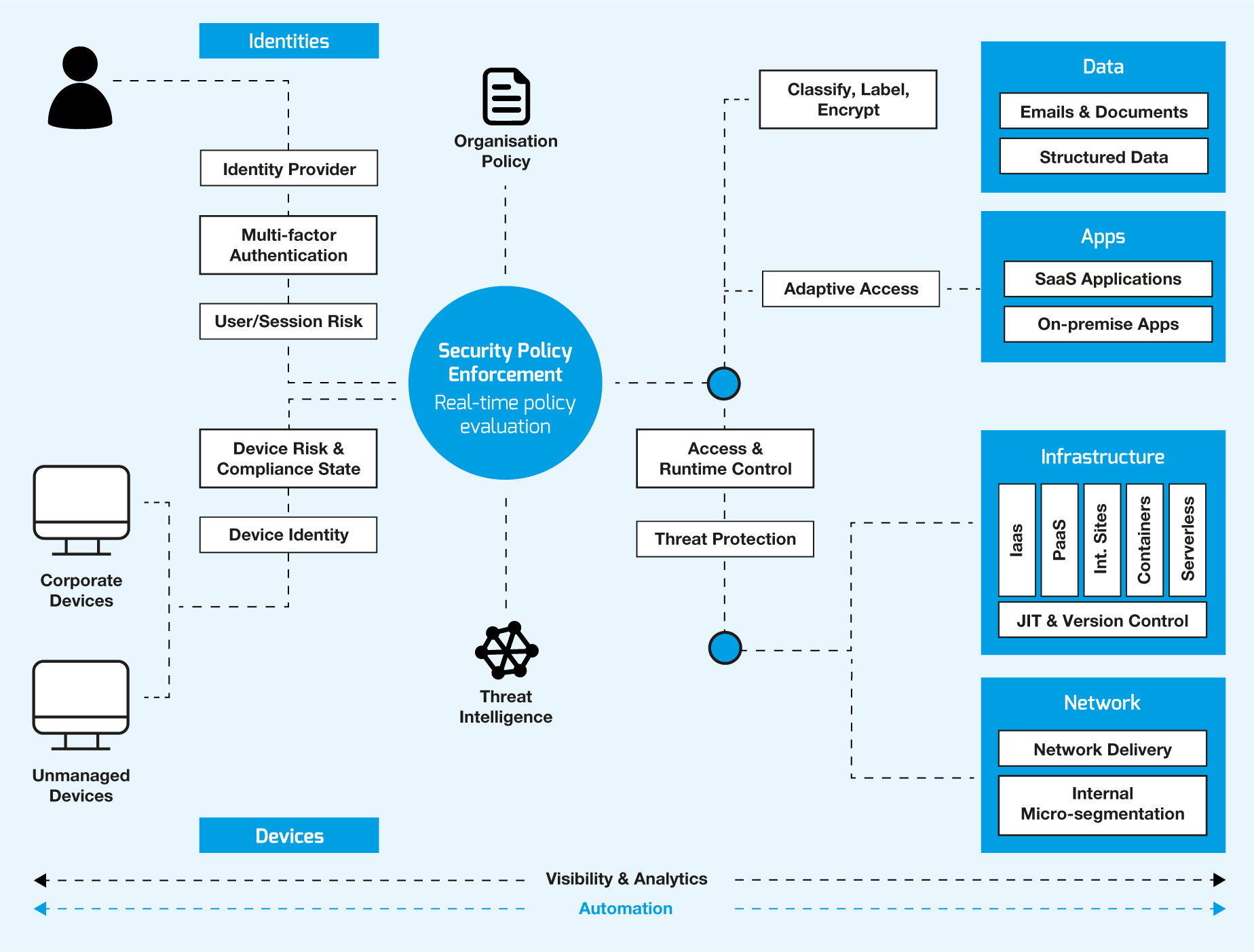
Secure Your Remote Workforce With Zero Trust Security NCi Technologies
https://www.ncitech.co.uk/media/1_1656_Original_6_Pillars_of_Zero_Trust_Diagram.png
A zero trust architecture ZTA is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data breaches and limit internal lateral movement This publication discusses ZTA its logical components possible deployment scenarios and threats Zero Trust is a security framework that requires all users whether in or outside the organization s network to be continuously authenticated authorized and validated before being granted access to network applications and data Zero Trust assumes that there is no traditional network edge networks can be local in the cloud or a hybrid cloud
[desc-10] [desc-11]
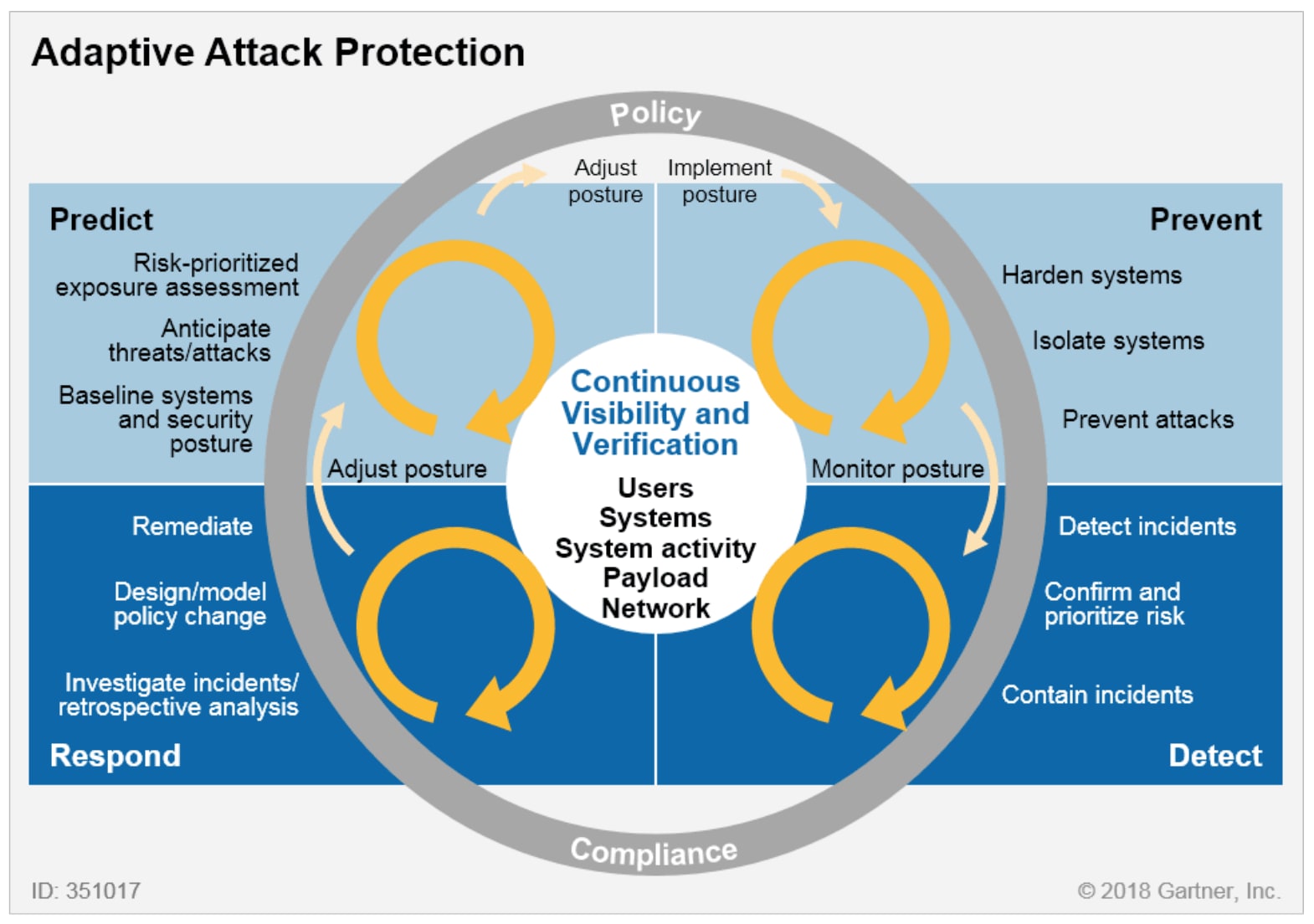
The Gartner CARTA Model
https://images.pingidentity.com/image/upload/f_auto,q_auto,w_auto,c_scale/ping_dam/content/dam/ping-6-2-assets/blogs/2021/0422/graphic-01.png

How To Prevent Supply Chain Attacks With The Zero Trust Architecture
https://assets-global.website-files.com/5efc3ccdb72aaa7480ec8179/60348a2493eb0b65867b651e_Figure 1.jpg

https://learn.microsoft.com › ... › zero-trust-overview
Understand the Zero Trust security model learn about the principles and apply the Zero Trust architecture using Microsoft 365 and Microsoft Azure services

https://csrc.nist.gov › pubs › sp › final
Zero trust ZT is the term for an evolving set of cybersecurity paradigms that move defenses from static network based perimeters to focus on users assets and resources A zero trust architecture ZTA uses zero trust principles to plan industrial and enterprise infrastructure and workflows

Using Zero Trust Principles To Protect Against Sophisticated Attacks

The Gartner CARTA Model
Zero Trust A Resilient IT In Times Of Cloud And Mobile Workplace

Implementing A Zero Trust Security Model At Microsoft

Zero Trust Networking Cohesive Networks
Zero trust Model zero Trust Network T Blog

Zero trust Model zero Trust Network T Blog
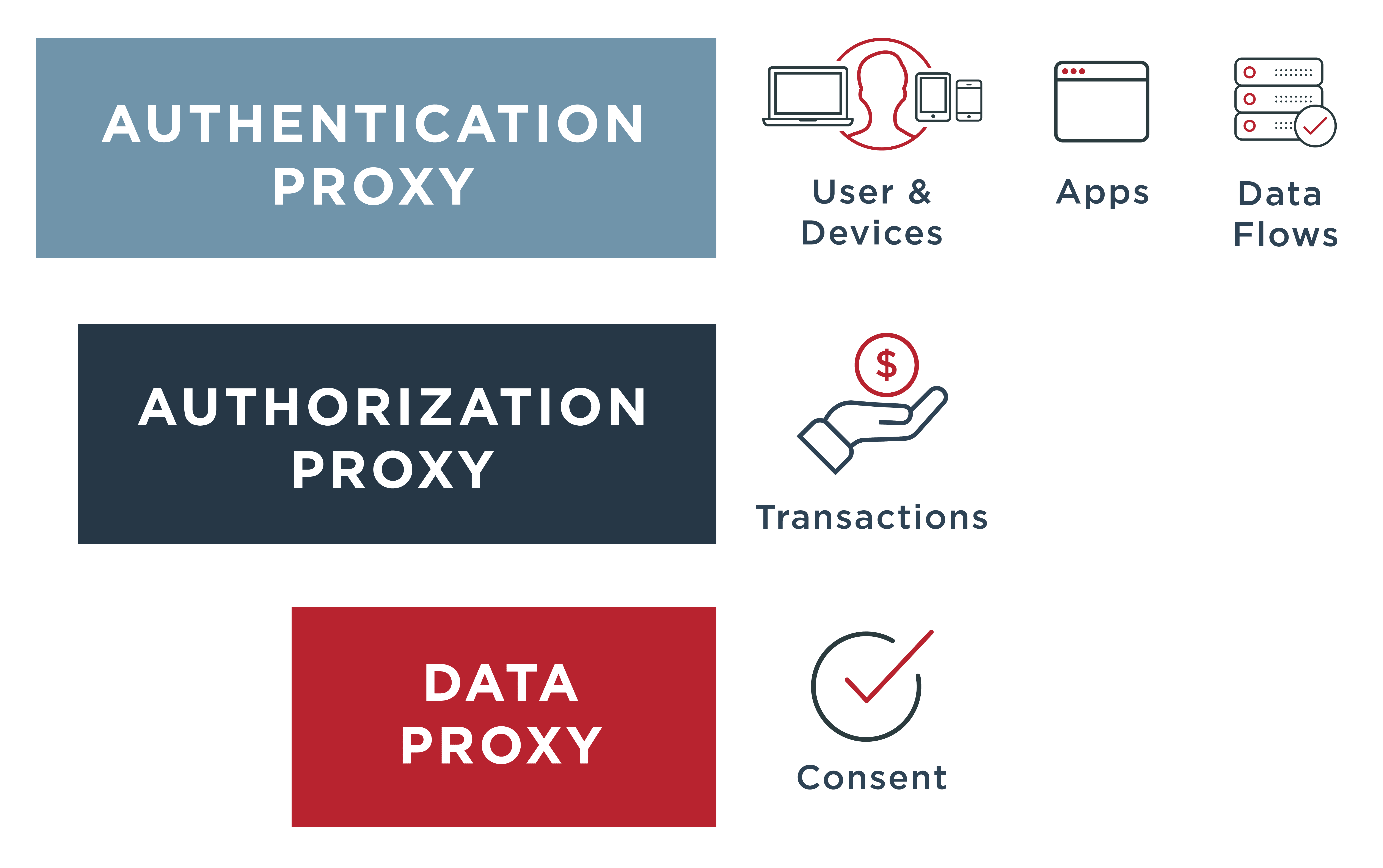
A Diagram Illustrating How Zero Trust API Security Includes An
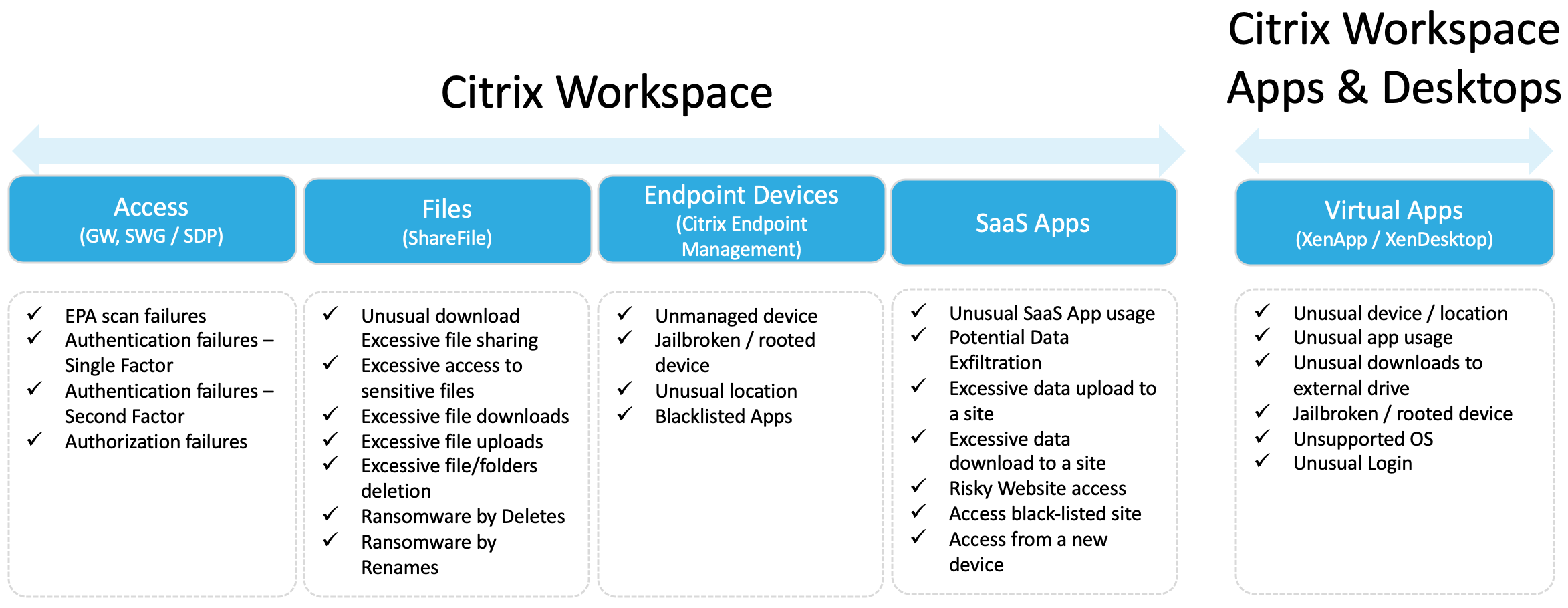
Tech Brief Zero Trust Citrix Tech Zone
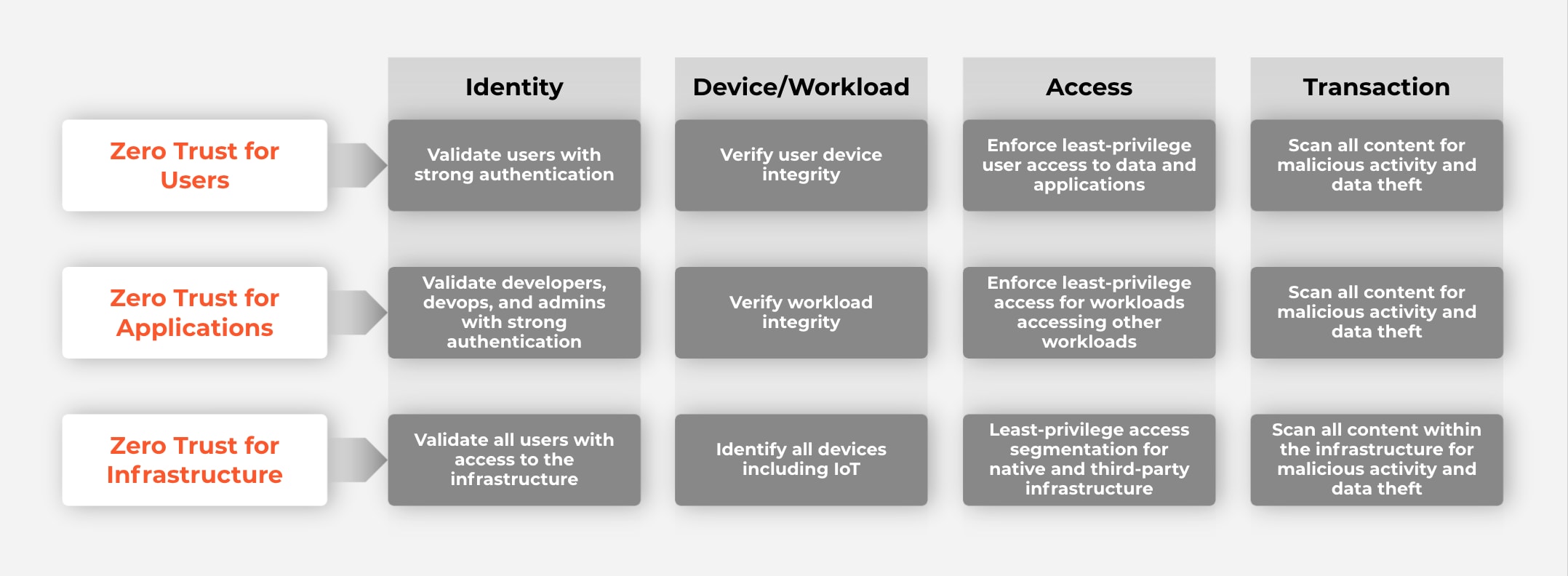
Zero Trust Short Answers To Agencies Top Questions Palo Alto
Zero Trust Requirements - [desc-12]